Written by forensic experts from the field, this book is the finest of all in exploring the art of Malware investigation in clear and concise manner. It offers in depth coverage of tools and technique used in live as well as static Malware analysis. Here is the table of contents of this book Chapter 1 […]
You are browsing archives for
Category: Security Books
Book of the Month : The Rookit ARSENAL
Wow…! This was my first reaction when I received this massive 900+ pages book from Amazon. I was just spell bounded and surprised to see such an enormous amount of information compiled on the lesser known area of computer security, the Rootkits. Here is the table of contents of this book, Part 1 Foundations Chapter 1 Setting […]
Book of the Month – Hacker’s Challenge 3
I always like reading about the real hacker stories from the field which are not only intriguing but offers great amount of insight and inspiration to draw from real attacks. One thing common about every hacker story is that it is unique and creative which are hard to find in any of the hacking books. […]
Book of the Month : Hacking – The Art of
This may sound like another hacking book written to sell, but it is not. This is one such book where author has covered everything from tip to toe of vulnerability exploitation, a complex topic to comprehend, in a simple and practical way. At a top level this book covers the following topics from security arena… […]
Book of the Month : 19 Deadly Sins of So...
This book is essential for anyone who is into software development to understand the basic security flaws as well as detect & eliminate them during the early development phase of the product itself. It offers detailed coverage on 19 crucial security flaws each explained in separate chapters. The book covers following 19 security flaws in […]
Book of the Month – Fuzzing: Brute Force
Fuzzing is the most powerful and quick method to expose the security flaws in any product. In that direction, this is the first book which attempted to cover all aspects of fuzzing. Written by prominent authors who mastered this field, the book not only explains the fundamentals but rich with practical examples too. Authors start […]
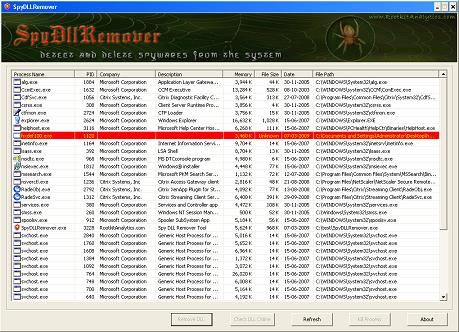
SpyDLLRemover : Detect & Delete Spywares
My new tool, SpyDLLRemover is released on the RootkitAnalytics website. This tool helps in detecting and deleting userland based rootkits which hide the processes and injected modules to prevent their detection from antirootkit softwares. Here is the snapshot of SpyDLLRemover detecting the hidden process belonging to HackerDefender Rootkit. Here is another snapshot of SpyDLLRemover detecting […]
Book of the Month : The Shellcoder’s Han
This is one of the best book written on most complex and interesting topics of computer security, ‘Discovering and Exploiting Security Holes’. It starts with explanation of different classes of security vulnerabilities such as stack overflows, heap overflows and format string bugs. Then it goes on describing the techniques to discover these flaws and then […]
Book of the month : ROOTKITS
This is the incredible book ever written on darkest area of computer security world. Authors have done splendid job in presenting the most mysterious subject of computer security in very simple and easy to understandable format. . . Here is the detailed table of contents…. 1. Leave No Trace. Understanding Attackers’ Motives. What Is a […]
Book of the Month : The IDA PRO
There has been many books written on the IDA Pro. But this book stands apart from all those. So far this is the most splendid book every produced on world’s most popular disassembler. . . Here is the ‘Table of Contents’ PART I: Introduction to IDA Chapter 1: Introduction to Disassembly Chapter 2: Reversing and […]