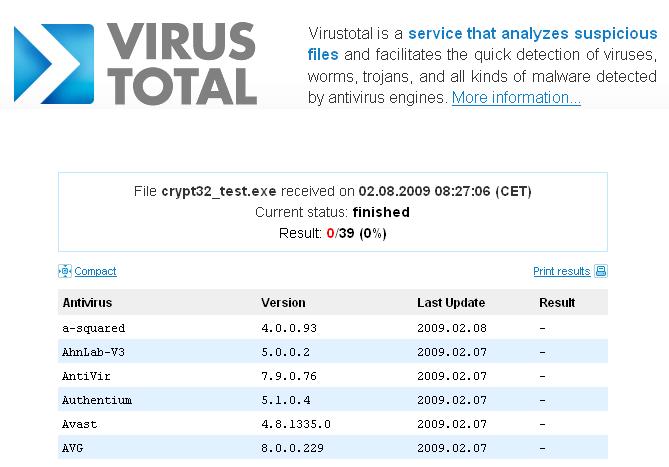
Now a days it is very common get infected even if you have best antivirus software installed with latest signatures. One of the main reason being is the rise in new category of viruses which does not belong to any previously detected virus families. Also the virus writing has become money making business rather than […]
Blog
Book of the month : ROOTKITS
This is the incredible book ever written on darkest area of computer security world. Authors have done splendid job in presenting the most mysterious subject of computer security in very simple and easy to understandable format. . . Here is the detailed table of contents…. 1. Leave No Trace. Understanding Attackers’ Motives. What Is a […]
HAKIN9 : Hardcore IT Security Magazine
Today I have received my first print copy of HAKIN9 magazine along with awesome T-Shirt. It is just amazing feeling to have stuff like this in my hands, its like mother holding her first baby. Hakin9 is the hardcore computer security magazine which exposes the top secrets straight from the field. Written by some of […]
Book of the Month : The IDA PRO
There has been many books written on the IDA Pro. But this book stands apart from all those. So far this is the most splendid book every produced on world’s most popular disassembler. . . Here is the ‘Table of Contents’ PART I: Introduction to IDA Chapter 1: Introduction to Disassembly Chapter 2: Reversing and […]
ProcHeapViewer with integrated search fe...
ProcHeapViewer 2.1, is a tool to scan process heaps now comes with integrated search feature which makes it easy to find ascii as well as unicode strings within the heap blocks. Also this new version has better user interface which not only gives it cool look & feel but makes it easy to use. The […]
Hacker Reversing Challenge 2008 Starting...
To all the hacker’s delight, the Hacker Reversing Challenge 2008 is back again with the bang. This challenge is carried out in three phases as in the last year and there is huge prize money for the winners as well as the participants. If you have participated in the last year’s challenge then you all […]
Virtualization Conference at IIT Bombay
Recently I had been to Virtualization conference, “Convergence 08“ held at IIT Bombay. This is the first ever technical event targeted at virtualization held so far in India with talks from industry experts in the field. Over 200 delegates from various organizations attended this two day event that focused on current research activitives in Virtualization. […]
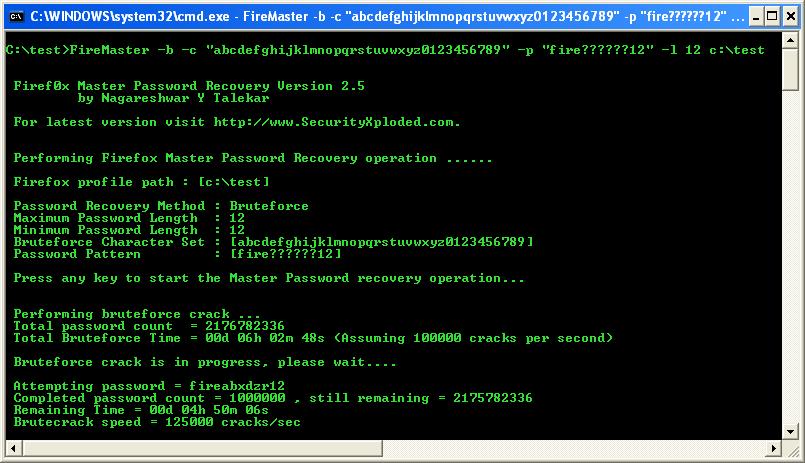
FireMaster with Pattern based Password R...
Pattern based password recovery is not new concept. However it has been used very rarely in the present day programs besides its importance and improvement it brings on the performance. It relies on the fact that each of us remembers some part of the password even though we have forgotten the password. This can be […]
New book on Reversing and IDA Pro
There is yet another book on the reversing arena which promises great deal of things. The books is titled “Reverse Engineering Code with IDA Pro” is set to release during the second week of February 2008. So far very few books have been released in the reverse engineering field. Also there is a need for […]
LDAPSearch with new Look
LDAPSearch is one of the simplest tool for remotely searching on the Directory servers such as eDirectory, Active Directory etc. Directory server provides the most scalable, high-performance LDAP data store for critical information within the industry and serves as the foundation for the new generation of e-business applications and Web services. In this context, this […]