Other day while I was crawling through the books at the local book mall, I just ran into this book. Immediately I popped up amazon site on my cell to check the ratings and found that its rated 4.5 (out of 11 ratings) which is a signal for must buy. Cloud computing being the hot […]
You are browsing archives for
Category: web security
Delivered Talk on ‘Application Virtualiz
I just came back after delivering presentation on ‘Application Virtualization’ during ‘Clouding Computing & Virtualization‘ summit at NITK Surathkal, one of the premiere engineering institute in India. It was great moment for me to deliver the talk at my own college after 6 years of passing out from here. The event was organized as educational […]
Password Secrets of Popular Windows Appl...
Here is the new article explaining about password secrets of some of the popular applications. It is going to explain about the password locations, storage techniques and encryption mechanism used by these applications. This application list has all category of applications such as Internet Browsers, Email Clients, Instant Messengers etc. Some of prominent applications include […]
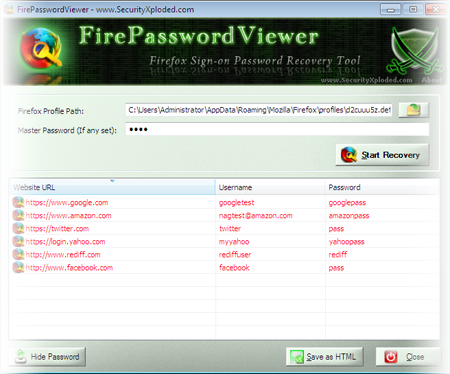
FirePasswordViewer Crossed 50K Download ...
FirePasswordViewer has crossed 50,000 downloads and it is the first tool from SecurityXploded.com to achieve this feat. FirePasswordViewer is the GUI version of popular FirePassword tool to recover stored sign-on passwords from Firefox. Like other browsers, Firefox also stores the login details such as username, password for every website visited by the user at the […]
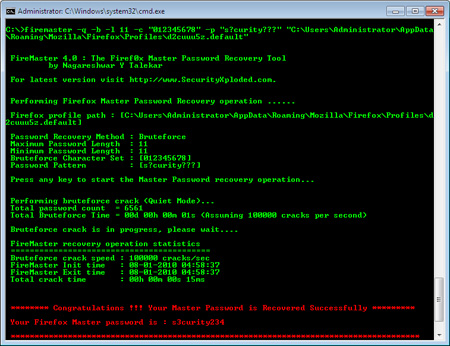
FireMasterLinux – Linux Port of FireMast
FireMasterLinux is the Linux port of popular FireMaster tool, an initiative by the elite members of “rainbowsandpwnies” security group. The team is headed byBroseidon along with fellow members. Currently base version of project is ready for Linux with the support for brute force password recovery. FireMaster is the first ever built tool to recover the […]
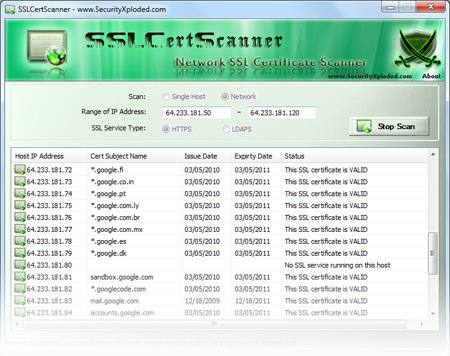
SSLCertScanner: New Tool to Scan for SSL...
SSLCertScanner is the FREE network based SSL certificate scanner software. It can remotely scan SSL certificate on any host which may present on the intranet or internet. It can also scan single host or multiple hosts at a time. Once the SSL certificate is discovered, SSLCertScanner automatically validates it by checking for expiry date. Here […]
Spammers have gone more Smarter
Spamming is most common thing today and its ardent task for any internet based application such as blogs, social networking sites to filter them out. Though these apps are doing good job but still spammers are coming with new ways to bypass these filters. Spams are getting more n more natural day by day which […]
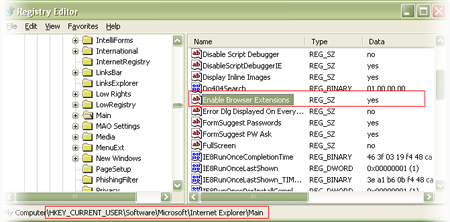
Quick Way to Enable/Disable BHO on the S...
BHO stands for Browser Helper Objects which are plugins written for Internet Explorer to enhance its capabilities. These plugins are basically DLLs which are loaded by IE during the start. But this feature is often misused by many spyware programs to monitor user’s browsing habits and steal the users credentials silently. Also some of the […]
Book of the Month – SQL Injection Attack
SQL Injection is one of the most popular web attacks that the security world has ever witnessed since the evolution of Internet. Till date it remains one of the less understood vulnerability from web security perspective as indicated by growing number of SQL injection attacks. In this direction, this book is set to clear apart […]