The web is full of recent DLL Hijacking Exploit after HDMoore and other security researchers have reported about numerous Windows applications suffering from these flaws. Here I have decided to put together simple version with all the relevant links at one place so that one gets the complete picture. . What is DLL Hijacking Vulnerability […]
You are browsing archives for
Category: Secure Coding
Book of the Month – SQL Injection Attack
SQL Injection is one of the most popular web attacks that the security world has ever witnessed since the evolution of Internet. Till date it remains one of the less understood vulnerability from web security perspective as indicated by growing number of SQL injection attacks. In this direction, this book is set to clear apart […]
Book of the Month : Writing Secure Code...
This is the one of the ‘Writing Secure Code’ series book completely focused on security design & implementations incorporated into vista. Written by experts involved in secure development of Vista, book offers complete coverage of security defenses in precise and concise format. However unlike earlier security book in the series, this book is solely dedicated […]
Book of the Month : Hacking – The Art of
This may sound like another hacking book written to sell, but it is not. This is one such book where author has covered everything from tip to toe of vulnerability exploitation, a complex topic to comprehend, in a simple and practical way. At a top level this book covers the following topics from security arena… […]
Book of the Month : 19 Deadly Sins of So...
This book is essential for anyone who is into software development to understand the basic security flaws as well as detect & eliminate them during the early development phase of the product itself. It offers detailed coverage on 19 crucial security flaws each explained in separate chapters. The book covers following 19 security flaws in […]
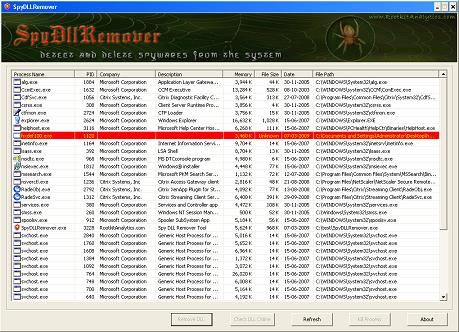
SpyDLLRemover : Detect & Delete Spywares
My new tool, SpyDLLRemover is released on the RootkitAnalytics website. This tool helps in detecting and deleting userland based rootkits which hide the processes and injected modules to prevent their detection from antirootkit softwares. Here is the snapshot of SpyDLLRemover detecting the hidden process belonging to HackerDefender Rootkit. Here is another snapshot of SpyDLLRemover detecting […]
Detecting System DLL …!
Recently while working on a new tool SpyDLLRemover, I had to separate out the operating system DLLs from others. To be precise, I needed method to reliably detect malicious DLL among all loaded DLLs of the process. This requires cornering out the malicious DLL by eliminating legitimate DLLs from the list. So I came up […]
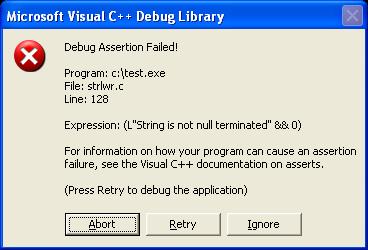
Have you crashed into _strlwr_s() ?
Almost every developer knows the cost of using insecure string function such as strcpy which can lead to buffer overflow exploits. But no one knows the cost of using the secure string functions. Here is just illustration of how much pain it can cause sometimes… Have a look at the sample code below, void main() […]