Wow…! This was my first reaction when I received this massive 900+ pages book from Amazon. I was just spell bounded and surprised to see such an enormous amount of information compiled on the lesser known area of computer security, the Rootkits. Here is the table of contents of this book, Part 1 Foundations Chapter 1 Setting […]
You are browsing archives for
Category: Reverse Engineering
ChromePasswordDecryptor – The Google Chr
Google Chrome browser is the latest entry into the ongoing web browsers war which is mainly ruled by IE and Firefox. Like other browsers Chrome also has built-in login password manager functionality which keeps track of the login secrets of all visited websites. ChromePasswordDecryptor is the tool which makes it easy to decrypt these login […]
Best Compiled List of WinDbg Commands
While crawling on the net for good list of Windbg commands, I have come across this site which has grouped together all essential commands. This makes it very easy to quickly figure out the required commands while you are deep into debugging… Here is the link to the page http://www.windbg.info/doc/1-common-cmds.html It is also available in […]
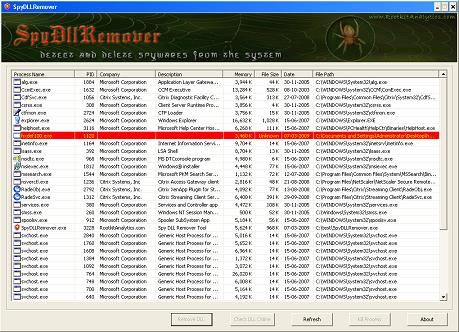
SpyDLLRemover : Detect & Delete Spywares
My new tool, SpyDLLRemover is released on the RootkitAnalytics website. This tool helps in detecting and deleting userland based rootkits which hide the processes and injected modules to prevent their detection from antirootkit softwares. Here is the snapshot of SpyDLLRemover detecting the hidden process belonging to HackerDefender Rootkit. Here is another snapshot of SpyDLLRemover detecting […]
RootkitAnalytics is Live Now
Finally RootkitAnalytics is on the world net now. Rootkit Analytics [RA] – the science of rootkit analysis, is a web-portal sculptured to enhance research, analysis and development of rootkit defense mechanisms. I am one of the lead member of RootkitAnalytics along with Ryan. Ryan specializes in Linux based rootkit analysis while I focus on Windows […]
Book of the Month : The Shellcoder’s Han
This is one of the best book written on most complex and interesting topics of computer security, ‘Discovering and Exploiting Security Holes’. It starts with explanation of different classes of security vulnerabilities such as stack overflows, heap overflows and format string bugs. Then it goes on describing the techniques to discover these flaws and then […]
Disabling Windows File Protection (SFC)
Lately I have been researching on Windows SFC (System File Checker) mechanism which is used to protect system files against accidental or deliberate modification. I have written about it in more detail as how this technique can be utilized to differentiate between system and normal components. Today while surfing on the net, I came across […]
Book of the Month : The IDA PRO
There has been many books written on the IDA Pro. But this book stands apart from all those. So far this is the most splendid book every produced on world’s most popular disassembler. . . Here is the ‘Table of Contents’ PART I: Introduction to IDA Chapter 1: Introduction to Disassembly Chapter 2: Reversing and […]
Hacker Reversing Challenge 2008 Starting...
To all the hacker’s delight, the Hacker Reversing Challenge 2008 is back again with the bang. This challenge is carried out in three phases as in the last year and there is huge prize money for the winners as well as the participants. If you have participated in the last year’s challenge then you all […]
New book on Reversing and IDA Pro
There is yet another book on the reversing arena which promises great deal of things. The books is titled “Reverse Engineering Code with IDA Pro” is set to release during the second week of February 2008. So far very few books have been released in the reverse engineering field. Also there is a need for […]