Today I have received my first print copy of HAKIN9 magazine along with awesome T-Shirt. It is just amazing feeling to have stuff like this in my hands, its like mother holding her first baby. Hakin9 is the hardcore computer security magazine which exposes the top secrets straight from the field. Written by some of […]
You are browsing archives for
Category: Computer Security
Hacker Reversing Challenge 2008 Starting...
To all the hacker’s delight, the Hacker Reversing Challenge 2008 is back again with the bang. This challenge is carried out in three phases as in the last year and there is huge prize money for the winners as well as the participants. If you have participated in the last year’s challenge then you all […]
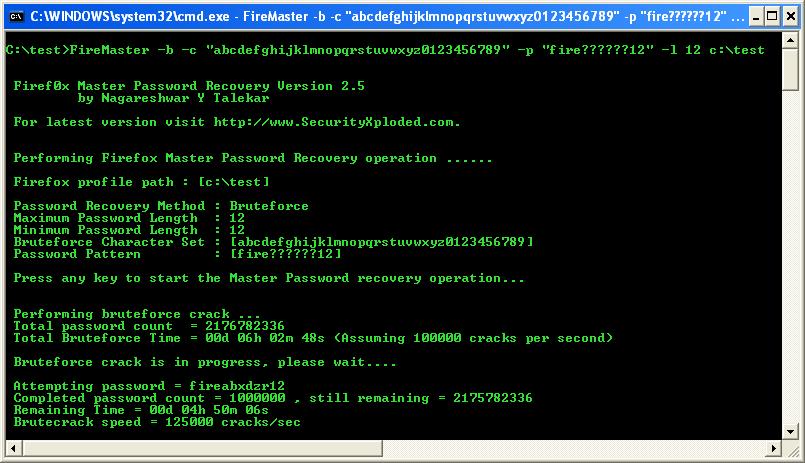
FireMaster with Pattern based Password R...
Pattern based password recovery is not new concept. However it has been used very rarely in the present day programs besides its importance and improvement it brings on the performance. It relies on the fact that each of us remembers some part of the password even though we have forgotten the password. This can be […]
New book on Reversing and IDA Pro
There is yet another book on the reversing arena which promises great deal of things. The books is titled “Reverse Engineering Code with IDA Pro” is set to release during the second week of February 2008. So far very few books have been released in the reverse engineering field. Also there is a need for […]
LDAPSearch with new Look
LDAPSearch is one of the simplest tool for remotely searching on the Directory servers such as eDirectory, Active Directory etc. Directory server provides the most scalable, high-performance LDAP data store for critical information within the industry and serves as the foundation for the new generation of e-business applications and Web services. In this context, this […]
Solution of Hacker Reversing Challenge 2...
This is the international reverse engineering challenge conducted by one of the U.S based security company. The purpose of this challenge is to evaluate the effectiveness of software protections. The contest is carried out in 3 phases where first and third phase involved breaking the protection of custom programs by using reverse engineering. One of […]
New AntiDebugging Timer Techniques
Almost everyone involved in the reverse engineering knows about the timer checks used for antidebugging. Generally functions such as GetTickCount or KeTickCount are used to detect and prevent any debugging attempts. Recently in the Hackers Reversing Challenge 2007, one of the less known timer checks have been used which makes use of functions QueryPerformanceFrequency & […]
F-Secure RE Challenge Conquered
F-Secure has announced new Reverse Engineering Challenge for the summer assembly event. The challenge is very interesting and neither easy nor difficult. It has 3 levels, at each level you have to find out email address which will take you to the next level. The challenge was announced a day back and already 18 people […]
Detecting & Defeating the Debuggers
Debuggers are the main tool used in reverse engineering. It is used by serial crackers to break the software protection or to uncover the algorithm used in the proprietary applications. On the other hand it is also used by researchers to analyze the malwares. Detecting the presence of debuggers is an important step in this […]
ProcHeapViewer : Faster way to enumerate...
ProcHeapViewer is a fast heap enumeration tool which uses better technique than normal Windows heap API functions. Its very useful tool for anyone involved in analyzing process heaps. Vulnerability researchers can find it useful while working on heap related vulnerabilities. Traditional Windows heap enumeration functions are slower and takes lot of time while traversing large […]