SQL Injection is one of the most popular web attacks that the security world has ever witnessed since the evolution of Internet. Till date it remains one of the less understood vulnerability from web security perspective as indicated by growing number of SQL injection attacks. In this direction, this book is set to clear apart […]
You are browsing archives for
Author: Administrator
Sniffing VoIP Calls Using UCSniff
Sniffing the neighbor’s passwords on the network was an age old stuff and every hacker would have done it at some point of time using tools such as Dsniff, cain & abel etc. Now you can record and listen to your neighbor’s phone calls too using the tool called UCSniff. Not just calls, you can […]
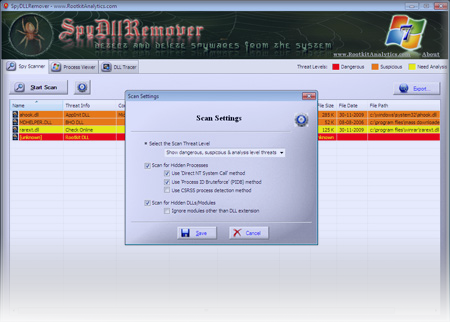
New SpyDLLRemover to Remove DLL from Sys...
The newer version of SpyDLLRemover v3.2 now support removal malicious DLL from system processes on Vista/Win7 platforms. Starting with Vista, Windows has introduced the session separation feature which prevents processes in one session interacting with process in another session. Normally all system processes including services live in session 0. All user session starts with session […]
NetworkPasswordDecryptor – New Tool to R
NetworkPasswordDecryptor is the free tool to instantly recover the network passwords stored in the ‘Credential Store’ of Windows. Not only Windows uses it to store network authentication passwords, but also other applications such as Outlook, Windows Live Messenger, Remote Destktop, Gmail Notifier etc uses it for storing their login passwords. NetworkPasswordDecryptor can recover following passwords […]
Google Offer Rewards for Chrome Hackers
Here comes the Google’s turn to offer bounty for hackers finding bugs in Chrome. As per the latest post “Encouraging More Chromium Security Research” on its official blog of Chrome, Google has decided to follow the practice of Microsoft and other organizations to reward the security researchers. For every Security vulnerability found in Chrome, Google […]
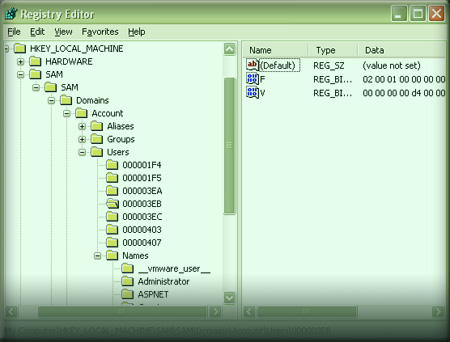
Discovering Hidden Registry Keys in Wind...
Windows uses registry to store every user and policy configuration on the system. One can directly tweak anything in the registry to alter any of the system settings. However not all registry keys are visible when viewed through default registry editor (regedit.exe). Especially some of the security and core system related keys are hidden from […]
Quick Password Recovery Using Rainbow Cr...
Some times back I have written article on using Rainbow crack to recover windows passwords. This article explains how one can crack any windows user passwords in seconds instead of regular brute force approach. In short, Rainbow crack involves comparing the password hash with precomputed hash tables called rainbow tables to find the matching plain […]
Social Engineering Made Easy by SET
“Man without tools is animal and with tools he is everything”. Till today the quote applies to every field man has set his footprints in. Man has created tools for everything to make every small job easier & quicker. Now we have tool for Social Engineering too. This new tool is called Social-Engineering Toolkit (in […]
Book of the Month – Professional Penetra
Here is the another good book in the field of penetration testing. Unlike other books which aims only at the technical aspects of Penetration testing, this one explains every step involved in the making of a Professional Pentester. Rather than just teaching how to use the existing tools, it does more splendid job of showcasing […]
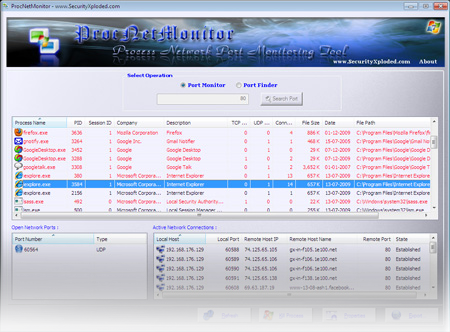
ProcNetMonitor – Process Network Port Mo
ProcNetMonitor, the tool for monitoring process network ports is supported for Windows 7 now. Newer version comes with enhanced user interface along with minor bug fixes. In short, ProcNetMonitor makes it easy to quickly analyze network activity of all running processes. It has advanced color based auto analysis system to make it easy to distinguish […]