This may sound like another hacking book written to sell, but it is not. This is one such book where author has covered everything from tip to toe of vulnerability exploitation, a complex topic to comprehend, in a simple and practical way. At a top level this book covers the following topics from security arena… […]
You are browsing archives for
Category: Vulnerability Research
Book of the Month : 19 Deadly Sins of So...
This book is essential for anyone who is into software development to understand the basic security flaws as well as detect & eliminate them during the early development phase of the product itself. It offers detailed coverage on 19 crucial security flaws each explained in separate chapters. The book covers following 19 security flaws in […]
Book of the Month – Fuzzing: Brute Force
Fuzzing is the most powerful and quick method to expose the security flaws in any product. In that direction, this is the first book which attempted to cover all aspects of fuzzing. Written by prominent authors who mastered this field, the book not only explains the fundamentals but rich with practical examples too. Authors start […]
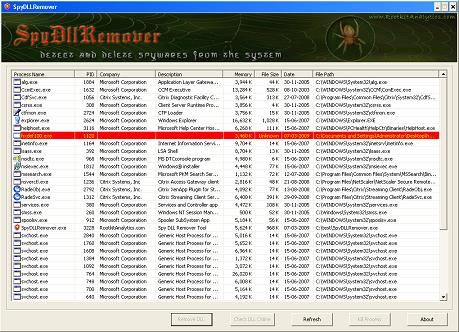
SpyDLLRemover : Detect & Delete Spywares
My new tool, SpyDLLRemover is released on the RootkitAnalytics website. This tool helps in detecting and deleting userland based rootkits which hide the processes and injected modules to prevent their detection from antirootkit softwares. Here is the snapshot of SpyDLLRemover detecting the hidden process belonging to HackerDefender Rootkit. Here is another snapshot of SpyDLLRemover detecting […]
Book of the Month : The Shellcoder’s Han
This is one of the best book written on most complex and interesting topics of computer security, ‘Discovering and Exploiting Security Holes’. It starts with explanation of different classes of security vulnerabilities such as stack overflows, heap overflows and format string bugs. Then it goes on describing the techniques to discover these flaws and then […]
ProcHeapViewer with integrated search fe...
ProcHeapViewer 2.1, is a tool to scan process heaps now comes with integrated search feature which makes it easy to find ascii as well as unicode strings within the heap blocks. Also this new version has better user interface which not only gives it cool look & feel but makes it easy to use. The […]
New book on Reversing and IDA Pro
There is yet another book on the reversing arena which promises great deal of things. The books is titled “Reverse Engineering Code with IDA Pro” is set to release during the second week of February 2008. So far very few books have been released in the reverse engineering field. Also there is a need for […]
ProcHeapViewer : Faster way to enumerate...
ProcHeapViewer is a fast heap enumeration tool which uses better technique than normal Windows heap API functions. Its very useful tool for anyone involved in analyzing process heaps. Vulnerability researchers can find it useful while working on heap related vulnerabilities. Traditional Windows heap enumeration functions are slower and takes lot of time while traversing large […]
Exploit Game : $$$ vs Vulnerability Re...
Charles Miller, security researcher at Independent Security Evaluators claims that he got the offer of $80,000 for remotely exploitable flaw in Linux, sighs that he could have asked for more. Though he could not get that price due to several conditions but finally managed to sell it for $50,000. He has written an interesting paper […]
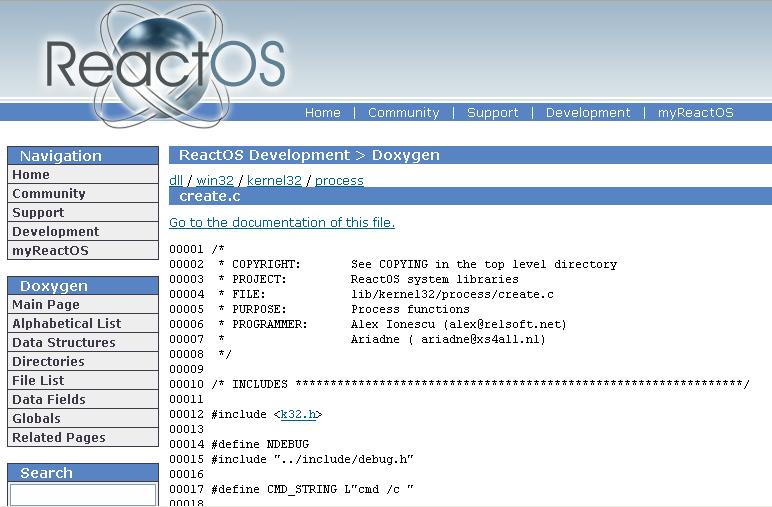
ReactOS : Source for Windows OS
ReactOS® is an advanced free open source operating system providing a ground-up implementation of a Microsoft Windows® XP compatible operating system. ReactOS is currently in its alpha stage and there is long way to go.Though its not exact replica of Windows XP, its near match. Moreover all function names are same as that of Windows. […]