DllHijackAuditor is the FREE tool to Audit against the DLL Hijacking Vulnerability for any Windows application. This is recently discovered critical security vulnerability affecting most of Windows systems. Currently large number of applications are currently susceptible to this vulnerability which can allow any attacker to completely take over the system. . In the first version […]
You are browsing archives for
Category: Pen Testing
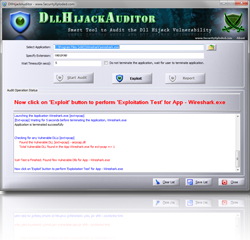
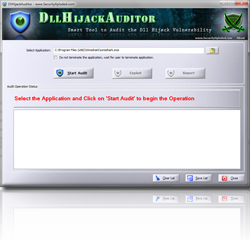
Presenting DllHijackAuditor – Smart Tool
DllHijackAuditor is the FREE tool to Audit against the DLL Hijacking Vulnerability for any Windows application. This is recently discovered critical security issue affecting almost all Windows systems on the planet. It appears that large amount of Windows applications are currently susceptible to this vulnerability which can allow any attacker to completely take over the […]
DLL Hijacking Exploit – All at One Plac
The web is full of recent DLL Hijacking Exploit after HDMoore and other security researchers have reported about numerous Windows applications suffering from these flaws. Here I have decided to put together simple version with all the relevant links at one place so that one gets the complete picture. . What is DLL Hijacking Vulnerability […]
Unleashing VASTO – A Virtualization Asse
VASTO is the first of its kind toolkit designed to asses the security of various Virtualization solutions including VMWare and Xen server. It is implemented as set of modules which can be integrated into Metasploit , the popular penetration testing framework. This makes it very easy for pen testers to directly integrate VASTO with their […]
SecurityXploded Tools on BackTrack
Today morning I have got surprise email from BackTrack team asking for consent to include our tools on BackTrack.They have also expressed interest to include some of our upcoming Linux versions such as FireMasterLinux. All these will be part of BackTrack repository and will be shipped in the next major release of BackTrack. BackTrack is […]
Password Secrets of Popular Windows Appl...
Here is the new article explaining about password secrets of some of the popular applications. It is going to explain about the password locations, storage techniques and encryption mechanism used by these applications. This application list has all category of applications such as Internet Browsers, Email Clients, Instant Messengers etc. Some of prominent applications include […]
Book of the Month – Wireshark Network An
“Wireshark Network Analysis” is the latest book on Wireshark, the top notch tool for network analyzer.Wireshark is used in analyzing network traffic, troubleshooting network problems on wired and wireless network. Either you are an network analyst, administrator, network security professional this will be the book that you don’t want to miss. The book is well […]
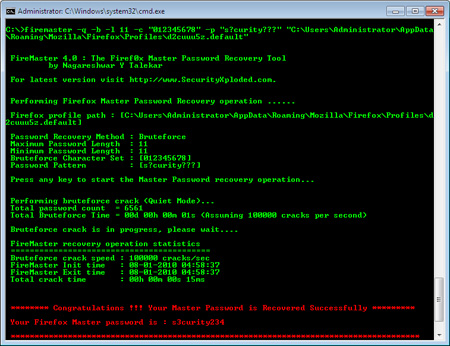
FireMasterLinux – Linux Port of FireMast
FireMasterLinux is the Linux port of popular FireMaster tool, an initiative by the elite members of “rainbowsandpwnies” security group. The team is headed byBroseidon along with fellow members. Currently base version of project is ready for Linux with the support for brute force password recovery. FireMaster is the first ever built tool to recover the […]
Book of the Month: NMAP COOKBOOK
“NMAP COOKBOOK – The fat-free guide to network scanning” is the latest book on the world’s best network scanning tool, NMAP. It is the most popular tool with pathora of options which works on wide range of platforms including Windows & Linux. NMAP is the most popular tool out there with so many options to […]
StreamArmor – New Tool to Scan & Sweep M
StreamArmor is the sophisticated tool for discovering hidden alternate data streams (ADS) as well as clean them completely from the system. It’s advanced auto analysis coupled with online threat verification mechanism makes it the best tool available in the market for eradicating the evil streams. It comes with fast multi threaded ADS scanner which can […]