Lately I have been researching on Windows SFC (System File Checker) mechanism which is used to protect system files against accidental or deliberate modification. I have written about it in more detail as how this technique can be utilized to differentiate between system and normal components. Today while surfing on the net, I came across […]
You are browsing archives for
Category: Hidden Myths
Detecting System DLL …!
Recently while working on a new tool SpyDLLRemover, I had to separate out the operating system DLLs from others. To be precise, I needed method to reliably detect malicious DLL among all loaded DLLs of the process. This requires cornering out the malicious DLL by eliminating legitimate DLLs from the list. So I came up […]
Online Virus Analysis
Now a days it is very common get infected even if you have best antivirus software installed with latest signatures. One of the main reason being is the rise in new category of viruses which does not belong to any previously detected virus families. Also the virus writing has become money making business rather than […]
Book of the month : ROOTKITS
This is the incredible book ever written on darkest area of computer security world. Authors have done splendid job in presenting the most mysterious subject of computer security in very simple and easy to understandable format. . . Here is the detailed table of contents…. 1. Leave No Trace. Understanding Attackers’ Motives. What Is a […]
New AntiDebugging Timer Techniques
Almost everyone involved in the reverse engineering knows about the timer checks used for antidebugging. Generally functions such as GetTickCount or KeTickCount are used to detect and prevent any debugging attempts. Recently in the Hackers Reversing Challenge 2007, one of the less known timer checks have been used which makes use of functions QueryPerformanceFrequency & […]
Detecting & Defeating the Debuggers
Debuggers are the main tool used in reverse engineering. It is used by serial crackers to break the software protection or to uncover the algorithm used in the proprietary applications. On the other hand it is also used by researchers to analyze the malwares. Detecting the presence of debuggers is an important step in this […]
Exploit Game : $$$ vs Vulnerability Re...
Charles Miller, security researcher at Independent Security Evaluators claims that he got the offer of $80,000 for remotely exploitable flaw in Linux, sighs that he could have asked for more. Though he could not get that price due to several conditions but finally managed to sell it for $50,000. He has written an interesting paper […]
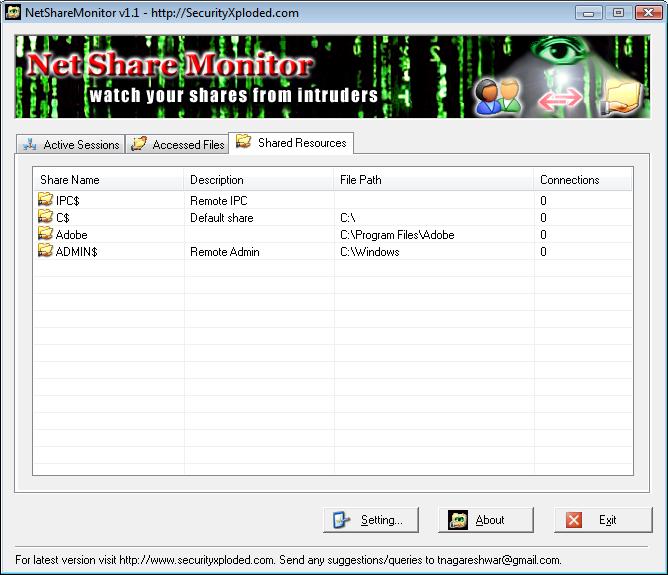
NetShareMonitor : Watch your shares from...
NetShareMonitor is the security tool to watch your shared files from the intruders and to protect your shares from unauthorized access. As soon as remote user connects to your machine, NetShareMonitor detects it and displays information about that session. The session information includes remote host address, remote user name, list of accessed files and time […]