Fuzzing is the most powerful and quick method to expose the security flaws in any product. In that direction, this is the first book which attempted to cover all aspects of fuzzing. Written by prominent authors who mastered this field, the book not only explains the fundamentals but rich with practical examples too. Authors start […]
You are browsing archives for
Category: Computer Security
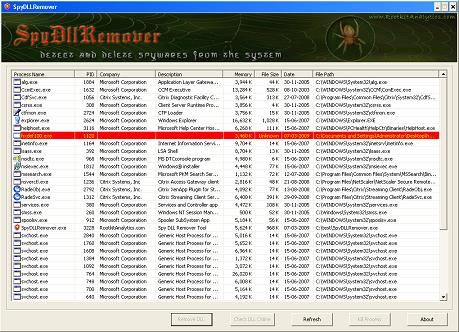
SpyDLLRemover : Detect & Delete Spywares
My new tool, SpyDLLRemover is released on the RootkitAnalytics website. This tool helps in detecting and deleting userland based rootkits which hide the processes and injected modules to prevent their detection from antirootkit softwares. Here is the snapshot of SpyDLLRemover detecting the hidden process belonging to HackerDefender Rootkit. Here is another snapshot of SpyDLLRemover detecting […]
RootkitAnalytics is Live Now
Finally RootkitAnalytics is on the world net now. Rootkit Analytics [RA] – the science of rootkit analysis, is a web-portal sculptured to enhance research, analysis and development of rootkit defense mechanisms. I am one of the lead member of RootkitAnalytics along with Ryan. Ryan specializes in Linux based rootkit analysis while I focus on Windows […]
Book of the Month : The Shellcoder’s Han
This is one of the best book written on most complex and interesting topics of computer security, ‘Discovering and Exploiting Security Holes’. It starts with explanation of different classes of security vulnerabilities such as stack overflows, heap overflows and format string bugs. Then it goes on describing the techniques to discover these flaws and then […]
Disabling Windows File Protection (SFC)
Lately I have been researching on Windows SFC (System File Checker) mechanism which is used to protect system files against accidental or deliberate modification. I have written about it in more detail as how this technique can be utilized to differentiate between system and normal components. Today while surfing on the net, I came across […]
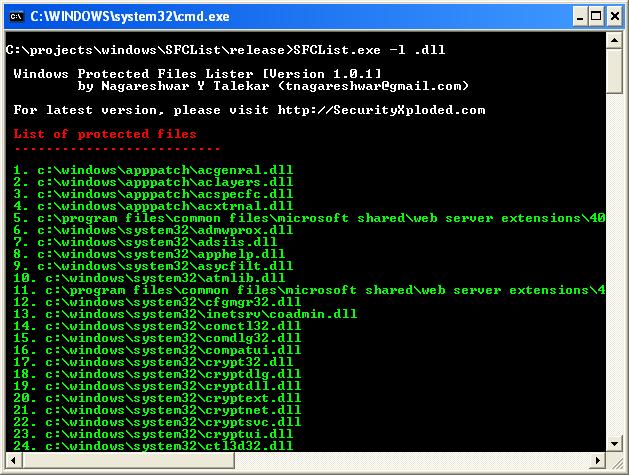
SFCList : Windows Protected Files Listin...
After I wrote about ‘Detecting System DLL’ some of my friends working on malware analysis asked for any tool which can show if the particular file is protected by SFC mechanism. I could not find any such tool and decided to write my own tool, SFCList. This tool helps to enumerate all those SFC protected […]
Detecting System DLL …!
Recently while working on a new tool SpyDLLRemover, I had to separate out the operating system DLLs from others. To be precise, I needed method to reliably detect malicious DLL among all loaded DLLs of the process. This requires cornering out the malicious DLL by eliminating legitimate DLLs from the list. So I came up […]
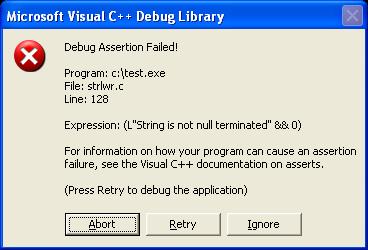
Have you crashed into _strlwr_s() ?
Almost every developer knows the cost of using insecure string function such as strcpy which can lead to buffer overflow exploits. But no one knows the cost of using the secure string functions. Here is just illustration of how much pain it can cause sometimes… Have a look at the sample code below, void main() […]
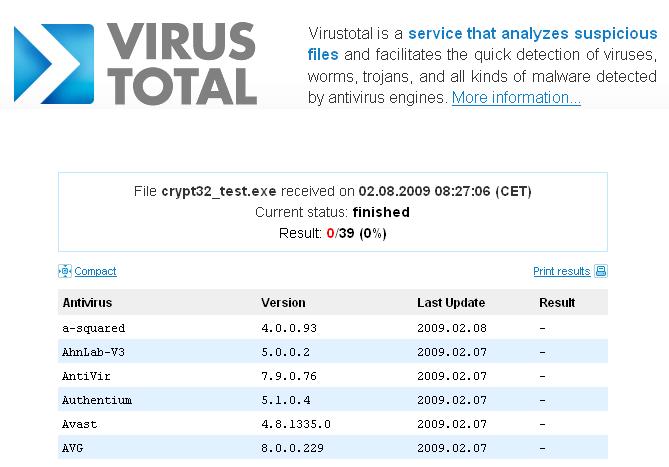
Online Virus Analysis
Now a days it is very common get infected even if you have best antivirus software installed with latest signatures. One of the main reason being is the rise in new category of viruses which does not belong to any previously detected virus families. Also the virus writing has become money making business rather than […]
Book of the month : ROOTKITS
This is the incredible book ever written on darkest area of computer security world. Authors have done splendid job in presenting the most mysterious subject of computer security in very simple and easy to understandable format. . . Here is the detailed table of contents…. 1. Leave No Trace. Understanding Attackers’ Motives. What Is a […]