Next time you open that PDF email attachment or PDF document from your friend, it may be the last time you will be owning your system. Next moment onwards it will no longer be yours because it will become part of botnet system controlled by attackers out there. Attackers are busy exploiting new launch action […]
You are browsing archives for
Category: Hacking
Book of the Month: NMAP COOKBOOK
“NMAP COOKBOOK – The fat-free guide to network scanning” is the latest book on the world’s best network scanning tool, NMAP. It is the most popular tool with pathora of options which works on wide range of platforms including Windows & Linux. NMAP is the most popular tool out there with so many options to […]
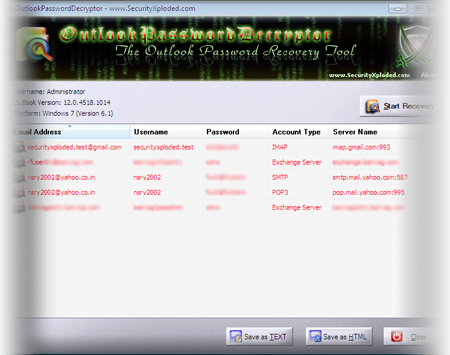
OutlookPasswordDecryptor – New Tool to R
OutlookPasswordDecryptor is the FREE tool to instantly recover lost password for all versions of Outlook Application.Different versions of Outlook store the password at different locations using different mechanism. OutlookPasswordDecryptor can decrypt all these passwords within fraction of second. It can not only recover the passwords of the current Outlook version but also from any earlier […]
Book of the Month – SQL Injection Attack
SQL Injection is one of the most popular web attacks that the security world has ever witnessed since the evolution of Internet. Till date it remains one of the less understood vulnerability from web security perspective as indicated by growing number of SQL injection attacks. In this direction, this book is set to clear apart […]
Sniffing VoIP Calls Using UCSniff
Sniffing the neighbor’s passwords on the network was an age old stuff and every hacker would have done it at some point of time using tools such as Dsniff, cain & abel etc. Now you can record and listen to your neighbor’s phone calls too using the tool called UCSniff. Not just calls, you can […]
Google Offer Rewards for Chrome Hackers
Here comes the Google’s turn to offer bounty for hackers finding bugs in Chrome. As per the latest post “Encouraging More Chromium Security Research” on its official blog of Chrome, Google has decided to follow the practice of Microsoft and other organizations to reward the security researchers. For every Security vulnerability found in Chrome, Google […]
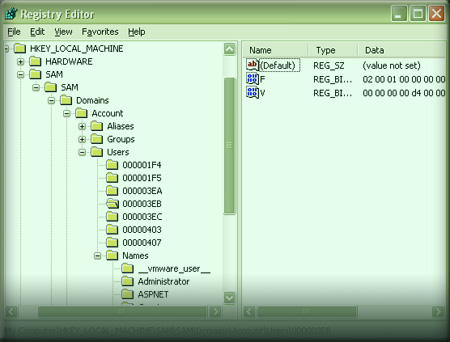
Discovering Hidden Registry Keys in Wind...
Windows uses registry to store every user and policy configuration on the system. One can directly tweak anything in the registry to alter any of the system settings. However not all registry keys are visible when viewed through default registry editor (regedit.exe). Especially some of the security and core system related keys are hidden from […]
Social Engineering Made Easy by SET
“Man without tools is animal and with tools he is everything”. Till today the quote applies to every field man has set his footprints in. Man has created tools for everything to make every small job easier & quicker. Now we have tool for Social Engineering too. This new tool is called Social-Engineering Toolkit (in […]
Operation Aurora – Google Got Hacked thr
Operation Aurora – The well targeted attack under which top companies including Google got hacked through the zero day vulnerability. Google has released separate statement recently illustrating nature of the attack vectors and motives of the attacker. In this attack which believed to be originated from China, the zero day (not publicly known) vulnerability in […]
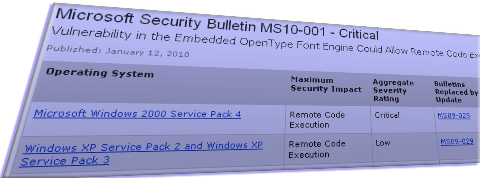
M$ Patches First Security Vulnerability ...
M$ has announced its first critical security vulnerability of the year 2010 in its Tuesday patch release. This is the vulnerability in the OpenType font engine embedded in the client applications which can lead to remote code execution leading to complete control of the system. As per the bulletin, the attack can be simulated by […]