This is the international reverse engineering challenge conducted by one of the U.S based security company. The purpose of this challenge is to evaluate the effectiveness of software protections. The contest is carried out in 3 phases where first and third phase involved breaking the protection of custom programs by using reverse engineering. One of […]
Blog
New AntiDebugging Timer Techniques
Almost everyone involved in the reverse engineering knows about the timer checks used for antidebugging. Generally functions such as GetTickCount or KeTickCount are used to detect and prevent any debugging attempts. Recently in the Hackers Reversing Challenge 2007, one of the less known timer checks have been used which makes use of functions QueryPerformanceFrequency & […]
Hypervisor @ FOSS.IN
One of the big event in the IT arena, FOSS.IN is taking place at Bangalore, the IT capital of India. It is fully packed with various presentations from big-wigs of open source community presenting some of the new stuffs and giving insight into the latest FOSS activities taking place across the world. I went […]
F-Secure RE Challenge Conquered
F-Secure has announced new Reverse Engineering Challenge for the summer assembly event. The challenge is very interesting and neither easy nor difficult. It has 3 levels, at each level you have to find out email address which will take you to the next level. The challenge was announced a day back and already 18 people […]
Detecting & Defeating the Debuggers
Debuggers are the main tool used in reverse engineering. It is used by serial crackers to break the software protection or to uncover the algorithm used in the proprietary applications. On the other hand it is also used by researchers to analyze the malwares. Detecting the presence of debuggers is an important step in this […]
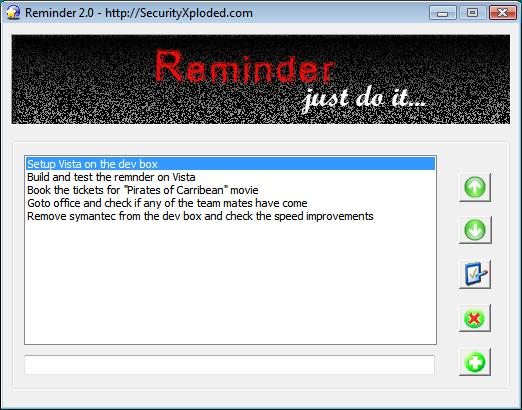
Reminder to remind your tasks
I have just finished with enhancing my old tool, Reminder. This tool keeps track of your day to day tasks and reminds you at regular intervals. Though this has nothing to do with security, it helps you to align your activities. I wrote this tool couple of years back for my own needs. Then some […]
ProcHeapViewer : Faster way to enumerate...
ProcHeapViewer is a fast heap enumeration tool which uses better technique than normal Windows heap API functions. Its very useful tool for anyone involved in analyzing process heaps. Vulnerability researchers can find it useful while working on heap related vulnerabilities. Traditional Windows heap enumeration functions are slower and takes lot of time while traversing large […]
Exploit Game : $$$ vs Vulnerability Re...
Charles Miller, security researcher at Independent Security Evaluators claims that he got the offer of $80,000 for remotely exploitable flaw in Linux, sighs that he could have asked for more. Though he could not get that price due to several conditions but finally managed to sell it for $50,000. He has written an interesting paper […]
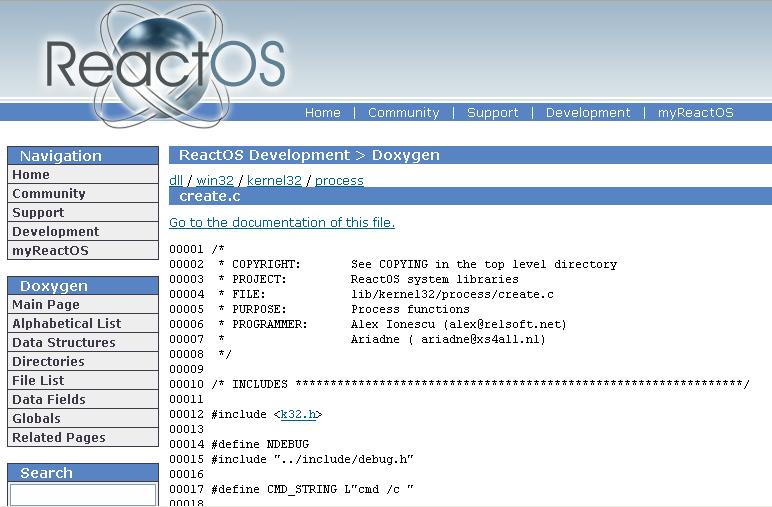
ReactOS : Source for Windows OS
ReactOS® is an advanced free open source operating system providing a ground-up implementation of a Microsoft Windows® XP compatible operating system. ReactOS is currently in its alpha stage and there is long way to go.Though its not exact replica of Windows XP, its near match. Moreover all function names are same as that of Windows. […]
iDefense kicks off new vulnerability res...
iDefense who created the waves in the security world by introducing the vulnerability research program has started new game for researchers to find out the remotely exploitable flaw in critical internet applications. The game is open for second & third quarters of this year giving ample time for researchers to find the vulnerability. Following are […]