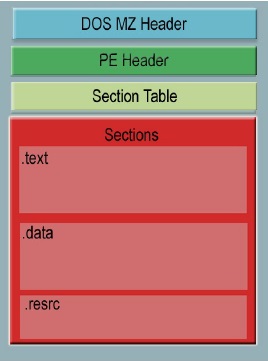
A win32 portable executable(PE) file consists of: DOS Header, PE Header, Section Table, Sections. Analyzing a PE file gives us a lot of information like the address in memory where the file will be located (ImageBase), address of entry point, imported and exported functions, packed or unpacked etc. Thus this static analysis can indicate whether […]
Blog
Using PEB to Get Base Address of Kernelb...
Process Environment Block (PEB) is a user mode data structure which applies over a whole process. It is designed to be used by the application-mode code in the operating system libraries, such as NTDLL.dll, Kernel32.dll. Through the use of PEB one can obtain the list of loaded modules, process startup arguments, ImageBaseAddress, heap address, check […]
SEH Exploitation to Get Shell Access
Structured Exception Handling is a mechanism for handling both hardware and software exceptions in Windows OS. Structured exception handling enables us to have complete control over the handling of exceptions and it also provides support for debuggers as well. SEH exploitation is based on stack buffer overflow technique. It becomes easy to exploit a […]
Our Local Security Meet [14th September ...
Talks: 09:30 – 10:15: Webworkers for Beginners – Prasanna K Web workers are long-running scripts that are not interrupted by user-interface scripts (scripts that respond to clicks or other user interactions). Keeping such workers from being interrupted by user activities should allow Web pages to remain responsive at the same time as they are running […]
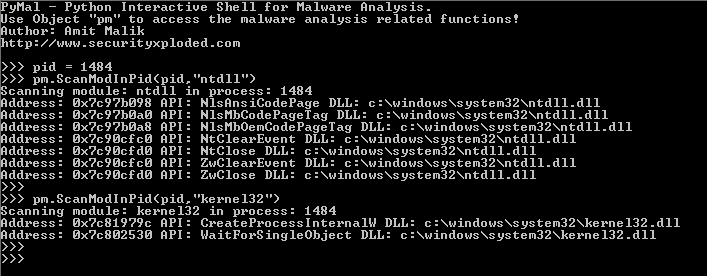
Bamital Analysis using Malpimp and Pymal
A couple of months ago, I released my two new tools Malpimp and PyMal for malware analysis. Malpimp aims at API tracing and PyMal is a general purpose malware analysis tool. In this blog I will discuss how to use both of them in malware analysis. As a case study I am using Bamital botnet […]
Advanced Malware Analysis Training Sessi...
Here is the quick update on this month’s Local Security meet (SX/Null/G4H/owasp) and our advanced malware training session on Introduction to Android This is part of our FREE ‘Advanced Malware Analysis Training’ series started from Dec 2012. In this session, Swapnil gave quick introduction to Android explaining technical details as well as various security […]
Our Local Security Meet on 24th August 2...
Talks: 09:30 – 10:00: WebSQL for Beginners – Prasanna K 10:00 – 10:10: Introductions 10:10 – 10:30: News bytes – Srinivas 10:30 – 11:00: Bit Coin Mining – Nikhil Kulkarni This talk would be about all you wanted to know about Bit Coins. Right from how it began, till how and where all it is […]
Announcing Results for the Student Mento...
We are very glad to announce the results of our mentorship programme, 2013. In the selection process we first shortlisted the participants on the basis of the answers they provided for questionnaire. The shortlisted candidates were then interviewed by our members. On the basis of their comments following students are selected for this programme. […]
Advanced Malware Analysis Training Sessi...
Here is the quick update on this month’s Local Security meet (SX/Null/G4H/owasp) and our advanced malware training session on Malware Memory Forensics. This is part of our FREE ‘Advanced Malware Analysis Training’ series started from Dec 2012. In this extended session, Monnappa explained extracting malware forensics artifacts from memory using Volatility – advanced memory […]
Advanced Malware Analysis Training Sessi...
Here is the quick update on this month’s Local Security meet (SX/Null/G4H/owasp) and our advanced malware training session on Sandbox Analysis. This is part of our FREE ‘Advanced Malware Analysis Training’ series started from Dec 2012. In this advanced session, Monnappa delivered extraordinary presentation on malware sandbox analysis explaining overview, architecture with examples. He […]