A couple of months ago, I released my two new tools Malpimp and PyMal for malware analysis. Malpimp aims at API tracing and PyMal is a general purpose malware analysis tool. In this blog I will discuss how to use both of them in malware analysis. As a case study I am using Bamital botnet sample.
Bamital is a good case study, it is using some innovative methods for code injection. Actually Bamital, carberp and zeroaccess all are interesting malware samples and are using some interesting and new code injection methods apart from their functionalities. Also it is interesting to see that most of the samples these days are using APC actively for code injection. So the systems that closely monitor CreateRemoteThread , nt/zwCreateThread etc. may not be able to catch these things. Anyways lets discuss a bit about bamital code injection technique. It hooks kernel32!WaitForSingleObject API in a very interesting way.
The procedure used by bamital is a bit similar to process hollowing. It first reads the kernel32.dll from remote process and then it patch the kernel32!WaitForSingleObject API with the hook handler code. Then it suspends the target process (explorer or browser) and unmap the kernel32.dll from the target process address space. It then maps the modified kernel32.dll back into the target process and resumes the process. As in most of the multi-threaded applications like explorer or browsers the call to WaitForSingleObject API is very frequent and hence it can execute its code without any delay.
Now in a traditional way when we want to hook something or we want to inject code into a remote process then either we have to allocate memory into another process or we have to load a dll into the remote process. But some intelligent HIPS and host based firewalls monitor remote process memory allocation and loading of a DLL, it means the older methods are basically already under observation so the method used by bamital is more stealthy. However this technique may crash the application if some thread in that process initiates execution before malware resumes the process. Bamital also hooks couple of other APIs but WaitForSingleObject API hooking is the interesting one.
API Tracing using Malpimp:
Lets use malpimp to trace the API calls of the malware. We can start malpimp from command line like: Malpimp.exe bamital.exe 0 – the second parameter (zero in this case) is basically the address from where we want to trace api calls, in case of zero, malpimp will trace the API calls from the initial execution point (address of entry point).
Bamital API trace:
Setting breakpoints on the exports of dll: C:\WINDOWS\system32\ntdll.dll Setting breakpoints on the exports of dll: C:\WINDOWS\system32\kernel32.dll RETURN ADDRESS: 0x004095af CALL FUNCTION: KERNEL32!GetSystemDefaultLCID RETURN ADDRESS: 0x004095bb CALL FUNCTION: KERNEL32!GlobalAlloc RETURN ADDRESS: 0x0040954c CALL FUNCTION: KERNEL32!CreateFileA yyyyyyyyy 401208 80000000 1 0 RETURN ADDRESS: 0x00409556 CALL FUNCTION: KERNEL32!GetProcAddress RETURN ADDRESS: 0x0040954c CALL FUNCTION: KERNEL32!CreateFileA yyyyyyyyy 401208 80000000 1 0 RETURN ADDRESS: 0x00409556 CALL FUNCTION: KERNEL32!GetProcAddress RETURN ADDRESS: 0x004095e5 CALL FUNCTION: KERNEL32!LoadLibraryA Spoolss.dll 40b205 Setting breakpoints on the exports of dll: C:\WINDOWS\system32\ADVAPI32.dll Setting breakpoints on the exports of dll: C:\WINDOWS\system32\WS2_32.dll RETURN ADDRESS: 0x004095f0 CALL FUNCTION: KERNEL32!GetProcAddress RETURN ADDRESS: 0x004095fe CALL FUNCTION: KERNEL32!GetLastError RETURN ADDRESS: 0x0040954c CALL FUNCTION: KERNEL32!CreateFileA yyyyyyyyy 401208 80000000 1 0 RETURN ADDRESS: 0x00409556 CALL FUNCTION: KERNEL32!GetProcAddress RETURN ADDRESS: 0x00409588 CALL FUNCTION: KERNEL32!VirtualProtect RETURN ADDRESS: 0x00409120 CALL FUNCTION: NTDLL!LdrLoadDll RETURN ADDRESS: 0x00409120 CALL FUNCTION: NTDLL!LdrLoadDll RETURN ADDRESS: 0x004091b5 CALL FUNCTION: KERNEL32!GetSystemDefaultLCID RETURN ADDRESS: 0x00407acf CALL FUNCTION: KERNEL32!VirtualAlloc RETURN ADDRESS: 0x00407d78 CALL FUNCTION: KERNEL32!CreateFileMappingA VIRTUALALLOC RETURNED POINTER 0x003c0000 RETURN ADDRESS: 0x00407d84 CALL FUNCTION: KERNEL32!GetLastError RETURN ADDRESS: 0x00407d9b CALL FUNCTION: KERNEL32!CloseHandle RETURN ADDRESS: 0x00407acf CALL FUNCTION: KERNEL32!VirtualAlloc RETURN ADDRESS: 0x00407acf CALL FUNCTION: KERNEL32!VirtualAlloc VIRTUALALLOC RETURNED POINTER 0x003d0000 RETURN ADDRESS: 0x00409251 CALL FUNCTION: KERNEL32!lstrcatA VIRTUALALLOC RETURNED POINTER 0x003e0000 RETURN ADDRESS: 0x0040925f CALL FUNCTION: KERNEL32!CreateDirectoryA C:\Documents and Settings\Administrator\Local Settings\Application Data\Windows Server 3e0000 0 RETURN ADDRESS: 0x00409271 CALL FUNCTION: KERNEL32!lstrcatA RETURN ADDRESS: 0x00409282 CALL FUNCTION: KERNEL32!lstrcatA RETURN ADDRESS: 0x004092a0 CALL FUNCTION: KERNEL32!CreateFileA C:\WINDOWS\system32\user32.dll 3c0000 80000000 1 0 RETURN ADDRESS: 0x004092b9 CALL FUNCTION: KERNEL32!GetFileTime RETURN ADDRESS: 0x004092c0 CALL FUNCTION: KERNEL32!CloseHandle RETURN ADDRESS: 0x00408e81 CALL FUNCTION: KERNEL32!lstrcatA RETURN ADDRESS: 0x00408ea4 CALL FUNCTION: KERNEL32!lstrcatA RETURN ADDRESS: 0x00408ec2 CALL FUNCTION: KERNEL32!CreateFileA C:\Documents and Settings\Administrator\Local Settings\Application Data\Windows Server\qauink.dll 3c0000 c0000000 3 0 RETURN ADDRESS: 0x00408ee9 CALL FUNCTION: KERNEL32!WriteFile RETURN ADDRESS: 0x00408f04 CALL FUNCTION: KERNEL32!SetFileTime RETURN ADDRESS: 0x00408f0f CALL FUNCTION: KERNEL32!CloseHandle RETURN ADDRESS: 0x00408f3d CALL FUNCTION: ADVAPI32!RegCreateKeyExA 80000001 Software\fgmdqauink 40b175 0 RETURN ADDRESS: 0x00408f62 CALL FUNCTION: ADVAPI32!RegSetValueExA RETURN ADDRESS: 0x00408f72 CALL FUNCTION: ADVAPI32!RegCloseKey RETURN ADDRESS: 0x00408f96 CALL FUNCTION: ADVAPI32!RegCreateKeyExA 80000002 SYSTEM\CurrentControlSet\Control\Session Manager\AppCertDlls 401086 0 RETURN ADDRESS: 0x00408fbd CALL FUNCTION: ADVAPI32!RegSetValueExA RETURN ADDRESS: 0x00408fcd CALL FUNCTION: ADVAPI32!RegCloseKey RETURN ADDRESS: 0x00409302 CALL FUNCTION: KERNEL32!GetModuleFileNameA RETURN ADDRESS: 0x00407acf CALL FUNCTION: KERNEL32!VirtualAlloc RETURN ADDRESS: 0x0040931f CALL FUNCTION: KERNEL32!lstrcatA VIRTUALALLOC RETURNED POINTER 0x003f0000 RETURN ADDRESS: 0x00409333 CALL FUNCTION: KERNEL32!MoveFileExA RETURN ADDRESS: 0x00409343 CALL FUNCTION: KERNEL32!MoveFileExA RETURN ADDRESS: 0x0040937f CALL FUNCTION: ADVAPI32!RegCreateKeyExA 80000002 SYSTEM\CurrentControlSet\Services\sr\Parameters 401008 0 RETURN ADDRESS: 0x0040939b CALL FUNCTION: ADVAPI32!RegSetValueExA RETURN ADDRESS: 0x004093a7 CALL FUNCTION: ADVAPI32!RegCloseKey RETURN ADDRESS: 0x004093cb CALL FUNCTION: ADVAPI32!RegCreateKeyExA 80000002 SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore 401038 0 RETURN ADDRESS: 0x004093dc CALL FUNCTION: ADVAPI32!RegDeleteValueA RETURN ADDRESS: 0x004093e8 CALL FUNCTION: ADVAPI32!RegCloseKey RETURN ADDRESS: 0x004081e2 CALL FUNCTION: KERNEL32!CreateToolhelp32Snapshot RETURN ADDRESS: 0x00408200 CALL FUNCTION: KERNEL32!Process32First RETURN ADDRESS: 0x00408216 CALL FUNCTION: KERNEL32!lstrcmpiA RETURN ADDRESS: 0x00408216 CALL FUNCTION: KERNEL32!lstrcmpiA RETURN ADDRESS: 0x00408216 CALL FUNCTION: KERNEL32!lstrcmpiA RETURN ADDRESS: 0x00408216 CALL FUNCTION: KERNEL32!lstrcmpiA RETURN ADDRESS: 0x00408250 CALL FUNCTION: KERNEL32!Process32Next RETURN ADDRESS: 0x00408216 CALL FUNCTION: KERNEL32!lstrcmpiA RETURN ADDRESS: 0x00408216 CALL FUNCTION: KERNEL32!lstrcmpiA RETURN ADDRESS: 0x00408216 CALL FUNCTION: KERNEL32!lstrcmpiA RETURN ADDRESS: 0x00408216 CALL FUNCTION: KERNEL32!lstrcmpiA RETURN ADDRESS: 0x00408250 CALL FUNCTION: KERNEL32!Process32Next RETURN ADDRESS: 0x00408216 CALL FUNCTION: KERNEL32!lstrcmpiA RETURN ADDRESS: 0x00408216 CALL FUNCTION: KERNEL32!lstrcmpiA RETURN ADDRESS: 0x00408216 CALL FUNCTION: KERNEL32!lstrcmpiA RETURN ADDRESS: 0x00408216 CALL FUNCTION: KERNEL32!lstrcmpiA RETURN ADDRESS: 0x00408250 CALL FUNCTION: KERNEL32!Process32Next RETURN ADDRESS: 0x00408216 CALL FUNCTION: KERNEL32!lstrcmpiA RETURN ADDRESS: 0x00408216 CALL FUNCTION: KERNEL32!lstrcmpiA RETURN ADDRESS: 0x00408216 CALL FUNCTION: KERNEL32!lstrcmpiA RETURN ADDRESS: 0x00408216 CALL FUNCTION: KERNEL32!lstrcmpiA RETURN ADDRESS: 0x00408250 CALL FUNCTION: KERNEL32!Process32Next RETURN ADDRESS: 0x00408250 CALL FUNCTION: KERNEL32!Process32Next RETURN ADDRESS: 0x00408250 CALL FUNCTION: KERNEL32!Process32Next RETURN ADDRESS: 0x00408250 CALL FUNCTION: KERNEL32!Process32Next RETURN ADDRESS: 0x00408250 CALL FUNCTION: KERNEL32!Process32Next RETURN ADDRESS: 0x00408250 CALL FUNCTION: KERNEL32!Process32Next RETURN ADDRESS: 0x00408250 CALL FUNCTION: KERNEL32!Process32Next RETURN ADDRESS: 0x00408250 CALL FUNCTION: KERNEL32!Process32Next RETURN ADDRESS: 0x00408250 CALL FUNCTION: KERNEL32!Process32Next RETURN ADDRESS: 0x00408250 CALL FUNCTION: KERNEL32!Process32Next RETURN ADDRESS: 0x00408250 CALL FUNCTION: KERNEL32!Process32Next RETURN ADDRESS: 0x00408250 CALL FUNCTION: KERNEL32!Process32Next RETURN ADDRESS: 0x00408250 CALL FUNCTION: KERNEL32!Process32Next RETURN ADDRESS: 0x004081e2 CALL FUNCTION: KERNEL32!CreateToolhelp32Snapshot RETURN ADDRESS: 0x00408200 CALL FUNCTION: KERNEL32!Process32First RETURN ADDRESS: 0x00408020 CALL FUNCTION: KERNEL32!OpenProcess PID: 1484 RETURN ADDRESS: 0x0040808f CALL FUNCTION: NTDLL!ZwCreateSection RETURN ADDRESS: 0x004080c2 CALL FUNCTION: KERNEL32!ReadProcessMemory RETURN ADDRESS: 0x00408183 CALL FUNCTION: NTDLL!ZwSuspendProcess RETURN ADDRESS: 0x004081c1 CALL FUNCTION: NTDLL!ZwResumeProcess RETURN ADDRESS: 0x00407ae6 CALL FUNCTION: KERNEL32!VirtualFree RETURN ADDRESS: 0x00407ae6 CALL FUNCTION: KERNEL32!VirtualFree RETURN ADDRESS: 0x00407ae6 CALL FUNCTION: KERNEL32!VirtualFree RETURN ADDRESS: 0x00407ae6 CALL FUNCTION: KERNEL32!VirtualFree RETURN ADDRESS: 0x00409616 CALL FUNCTION: KERNEL32!ExitProcess
In the api trace we can see that the malware opened a process and after couple of API calls it just terminates. So here is the indication that the malware may have injected its code into the remote process.
We can now use pymal to start our analysis on the process which was opened by the malware. Pymal offers couple of good functions for malware analysis but hook detection and injected code detection are the powerful ones.
Hook detection using PyMal:
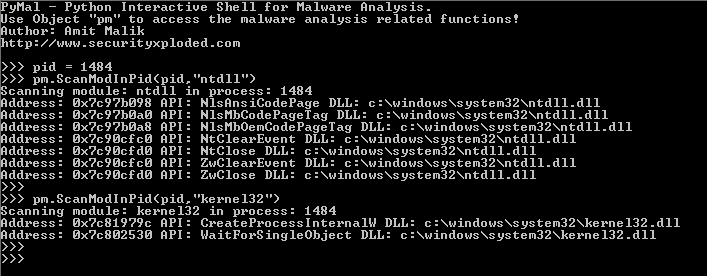
ScanModInPid method can be used to check a loaded module for hooks in a process. PyMal also offers couple of other methods that can scan the entire process and even the entire system for hooks. But we will use ScanModInPid, it takes pid and module name as a parameter as you can see in the below snapshot.
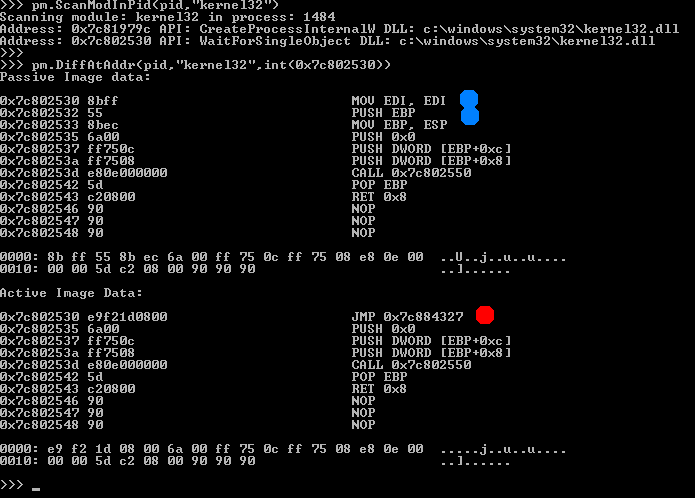
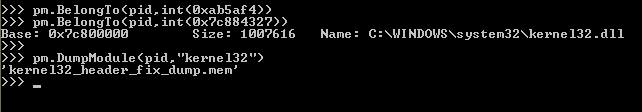
As you can see in the snapshots that couple of APIs from ntdll.dll and kernel32.dll are hooked. Now our job is to identify the modules or code segment where these hooks are pointing. Pymal offers a BelongTo method to detect which module holds the hook’s address. If the address is in any loaded module then it will report the name of the DLL but if it will not report anything then it means that the address is from a newly allocated region.
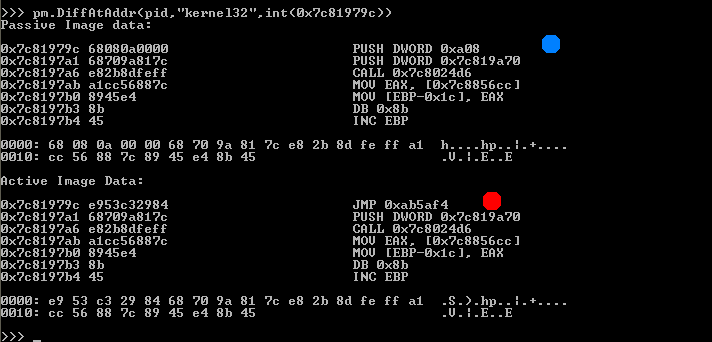
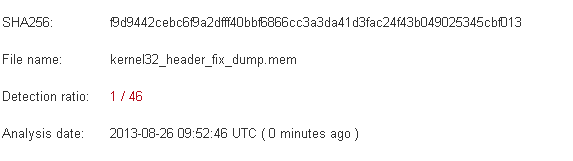
As you can in the above snapshot that the hook address for CreateProcessInternalW is from a newly allocated region and hook address for WaitForSingleObject is from kernel32.dll itself. It basically indicates that some code is injected into the kernel32.dll address space as well. Using pymal’s DumpModule method we can dump the kernel32.dll from process to disk as shown in the below snapshot. After it we can also upload the file to virustotal or manually inspect the strings and codes.
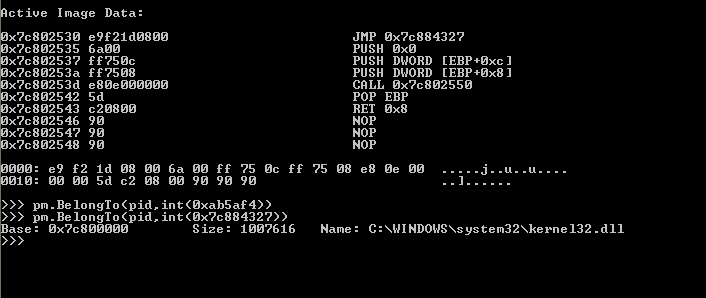
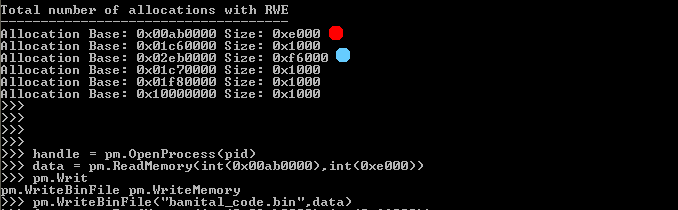
Now we know that the hook address for CreateProcessInternalW is from a newly allocated region but we don’t know the allocation size and base address. So we can use pymal‘s GetAllocation method or FindInjectedCode method to find allocation base address and size. For several reasons I prefer FindInjectedCode method over GetAllocation.
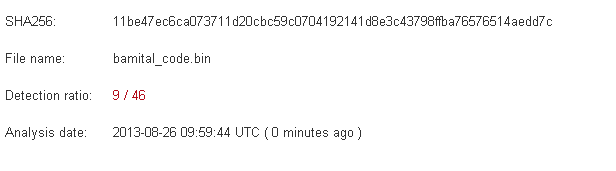
As you can see in the above snapshot that our hook address is from marked allocation, after that we can read this allocation from process and can search for strings or can write the data on the disk.
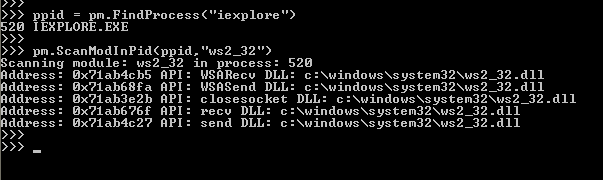
In Internet explorer it will also hook couple of ws2_32.dll APIs.
You can download the malpimp and Pymal from the following links:
Malpimp: http://securityxploded.com/malpimp.php
Pymal: http://securityxploded.com/pymal.php
Pymal Demo Video: http://vimeo.com/67400713
Also if you are a beginner then you may want to visit our free malware analysis course page: http://securityxploded.com/security-training.php

No Comments Yet