Here comes our new SecurityPhresh Beta edition. Since last couple of months we have been actively working on it. Here are some of the highlights, Redesigned Back-end Engine At the forefront was the fully automated back-end engine which was completely redesigned from scratch and Amit did very fine job in bringing it up in short […]
You are browsing archives for
Author: Administrator
Nullcon Delhi 2012
Null as we know is an open security community and organizes international security conference Nullcon every year. Usually the conference was being held in Goa for the past three times. But this time the conference also took place in Delhi for the first time. The conference was to start from 26 of September to 29 […]
New Tool – LDAP Password Kracker
Here comes our 91st new tool – LDAP Directory Kracker . Useful tool to recover the lost password from any of the LDAP based Directory Servers. Many companies, universities use Directory Servers to store sensitive information such as employee account details, salary, trade secrets etc. In this direction, this tool can greatly help Penetration testers […]
Stealing iPhone Backups using Metasploit
Introduction to iPhone Backups: iTunes is used to back up the iPhone data to a computer. iTunes backup makes a copy of everything on the device like contacts, SMS, photos, calendar, music, call logs, configuration files, database files, keychain, network settings, offline web application cache, safari bookmarks, cookies and application data, etc. It also backups […]
Reversing Training Session Part 11 – Exp
Here is the quick update on this month’s Local Security meet (SX/Null/G4H/owasp) where Amit has delivered one of his best session on ‘Practical Reversing VI – Exploit Development Advanced’. This is part of our ongoing FREE ‘Reversing & Malware Analysis Training’ started since our Jan 2012 meet. Today we had solid response from the crowd […]
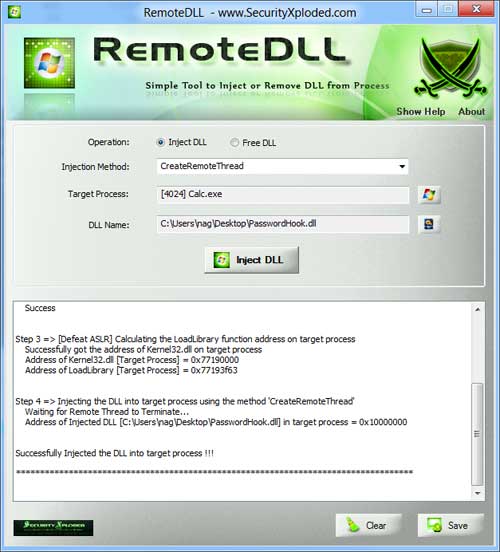
DLL Injection and Windows 8
Recently while working on new version of RemoteDLL, I discovered interesting changes around DLL injection on Windows 8. Before I actually talk about new changes, here is little background story. CreateRemoteThread is most common method used for DLL injection. It used to work flawlessly till Windows XP. However since Vista, it changed the colors, mainly […]
Released JDownloaderPasswordDecryptor v2...
Here is the delightful news for all JDownloader fans. We have just released new version of JDownloader Password Decryptor v2.0 which supports password recovery from latest JDownloader 2 Beta edition. Over the last couple of months we have received numerous requests to support JDownloader 2 beta version. Some of them even sent us account config […]
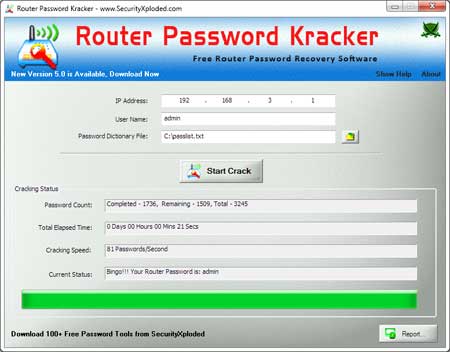
Released New Tool – Router Password Krac
Here comes our 90th Free Tool – Router Password Kracker. It is free tool to quickly recover lost password from Router, Modem or Website protected with HTTP BASIC Authentication. It comes with simple and cool GUI interface making it easier for everyone from layman to expert. Also Penetration Testers and Forensic Investigators can find this […]
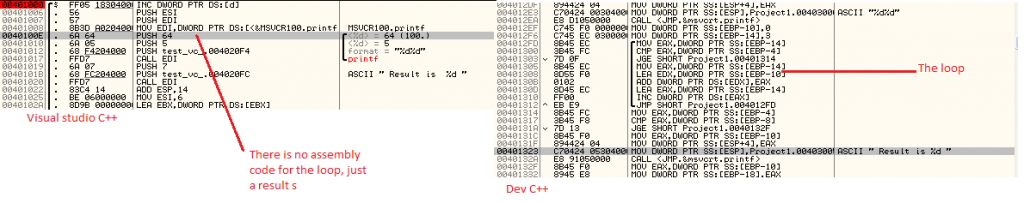
Demystifying Compiler Optimization – Dif
I analyzed some simple source code examples running in visual C++ (without optimization option) and Dev C++. I saw that VC++ code is slightly optimized then DEV C++. The following code shows the difference between function calls on both the compilers. In visual C++: push eax mov ecx, [local.1] push ecx call F Dev C++: […]
Training Session Part 10 – Practical Rev
Here is the quick update from our this month’s Local Security meet (sx/null/g4h/owasp) where Harsimran/Amit had delivered a splendid session on ‘Practical Reversing V – Exploit Development Basics’. This is part of our ongoing FREE ‘Reversing & Malware Analysis Training’ started since our Jan 2012 meet. Harsimran was supposed to deliver this presentation. However […]




![Reversing Training Session Part 11 – Exploit Development [Advanced]](https://securityxploded.com/images/training-reversing-session9_main.jpg)