Introduction to iPhone Backups: iTunes is used to back up the iPhone data to a computer. iTunes backup makes a copy of everything on the device like contacts, SMS, photos, calendar, music, call logs, configuration files, database files, keychain, network settings, offline web application cache, safari bookmarks, cookies and application data, etc. It also backups […]
You are browsing archives for
Category: Reverse Engineering
Reversing Training Session Part 11 – Exp
Here is the quick update on this month’s Local Security meet (SX/Null/G4H/owasp) where Amit has delivered one of his best session on ‘Practical Reversing VI – Exploit Development Advanced’. This is part of our ongoing FREE ‘Reversing & Malware Analysis Training’ started since our Jan 2012 meet. Today we had solid response from the crowd […]
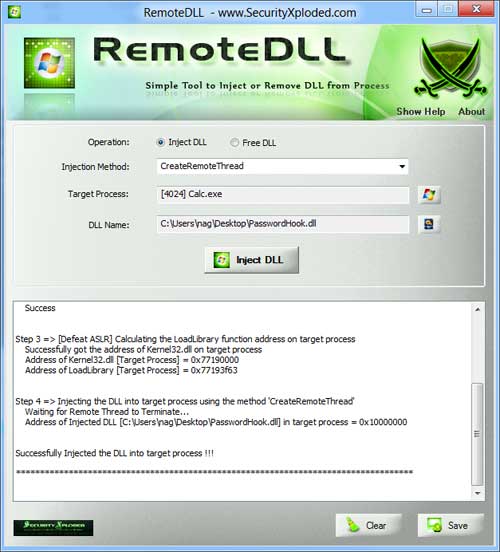
DLL Injection and Windows 8
Recently while working on new version of RemoteDLL, I discovered interesting changes around DLL injection on Windows 8. Before I actually talk about new changes, here is little background story. CreateRemoteThread is most common method used for DLL injection. It used to work flawlessly till Windows XP. However since Vista, it changed the colors, mainly […]
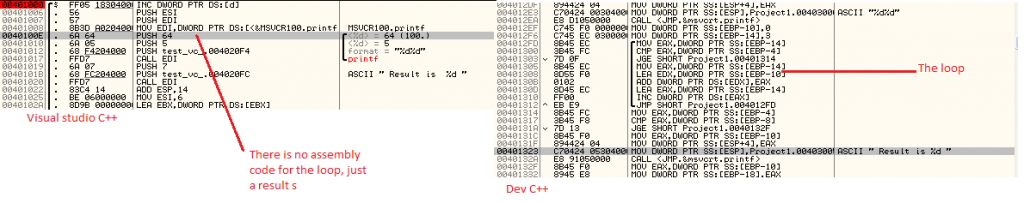
Demystifying Compiler Optimization – Dif
I analyzed some simple source code examples running in visual C++ (without optimization option) and Dev C++. I saw that VC++ code is slightly optimized then DEV C++. The following code shows the difference between function calls on both the compilers. In visual C++: push eax mov ecx, [local.1] push ecx call F Dev C++: […]
Training Session Part 10 – Practical Rev
Here is the quick update from our this month’s Local Security meet (sx/null/g4h/owasp) where Harsimran/Amit had delivered a splendid session on ‘Practical Reversing V – Exploit Development Basics’. This is part of our ongoing FREE ‘Reversing & Malware Analysis Training’ started since our Jan 2012 meet. Harsimran was supposed to deliver this presentation. However […]
Using ShellDetect for Shellcode Analysis...
Some people queried me about ShellDetect specifically, how it works or how they can use it for shellcode analysis and detection. Shelldetect is the result of a short term research programme, I was actually trying to build a tool that can detect shellcode using the dynamic analysis apart from applying GetPC heuristics or some similar […]
Training Session Part 7 – Practical Reve
Here is the quick update from our this month’s Local Security meet (sx/null/g4h/owasp) where Nagareshwar did splendid session on ‘Practical Reversing (II) – Unpacking. This is part of our ongoing FREE ‘Reversing & Malware Analysis Training’ started since our Jan 2012 meet. In this interesting practical session, he demonstrated How to manually unpack UPX packed […]
Training Session Part 5 – Reverse Engine
Here is the quick update from our monthly security meet (sx/null/g4h/owasp) where Swapnil did splendid session on ‘Reverse Engineering Tools Basics’. This is part of our ongoing FREE ‘Reversing & Malware Analysis Training’ started since our Jan 2012 meet. In this practical session, he demonstrated top reversing tools OllyDbg, IDA Pro, PEditor, PEiD etc. Along […]
Released Shell Detect v1.1 – Now Detects
Shell Detect is the FREE tool to detect presence of Shell Code within a file or network stream. You can either provide raw binary file (generated from Metasploit) or network stream file as input to this tool. These days attackers distribute malicious files which contains hidden exploit shell code. This can hijack your system if […]
Assembly Programming Basics Presentation...
Here comes the update from our last local security meet (sx/null/g4h/owasp) where Amit Malik & Swapnil delivered spectacular session on ‘Assembly Programming Basics’. This is part of our ongoing FREE ‘Reversing & Malware Analysis Training’ which has been started since our last meet. Duo delivered superb one hour session to jam packed 40+ folks who […]


![Reversing Training Session Part 11 – Exploit Development [Advanced]](https://securityxploded.com/images/training-reversing-session9_main.jpg)