The danger of catching a computer virus is constant trouble for every computer user. Viruses affect business operations, your computer’s functioning, data safety, and many other cases where third-party cybercriminals can profit from your private information. Malware attacks happen annually, even in big businesses like Facebook, Quora, Marriott, and others, as 133% of records became […]
Blog
How to Bring Best of Your Parenting in 2...
With the New Year comes that tingle to wind up a better than ever you. Some make goals to exercise more, some to spend less cash, for some being organized is much more than everything in the upcoming New Yearor become less time waster. But, real question to be asked yourself is how […]
Microsoft MCSE Certification: Your Next ...
Microsoft MCSE is the most in-demand certification for all those professionals who work in the Information Technology industry. Most IT companies prefer hiring those workers who carry the Microsoft MCSE certificate. That is why most of the IT job applicants today try to get certified by Microsoft. In the competitive job market, MCSE helps an […]
Computer Security Tips: Stay Safe Online
In recent times cyber security has raised the level of awareness and public consciousness as never before. Both large corporations and big organizations try to take care of online security as much as they can. That’s why cyber criminals and hackers have focused more on smaller companies and single entrepreneurs. This awful tendency leads to […]
SecurityXploded Mentorship Programme 201...
I am writing this blog to share my SecurityXploded Student Mentorship Programme experience with the future students of this programme. My mentorship programme started last year in August when I was in 2nd year of MS at IIIT-Allahabad. I knew about SecurityXploded community since I used to follow their blogs, training programmes and security tools […]
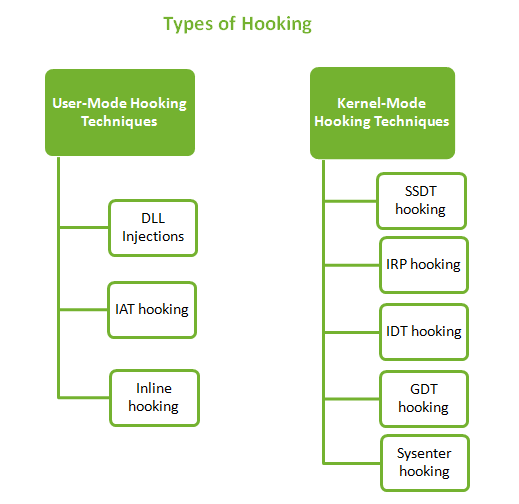
Code Injection and API Hooking Technique...
Hooking covers a range of techniques used for many purposes like debugging, monitoring, intercepting messages, extending functionality etc. Hooking is also used by a lot of rootkits to camouflage themselves on the system. Rootkits use various hooking techniques when they have to hide a process, hide a network port, redirect file writes to some different […]
Announcement – SecurityXploded Security
From the past two years we are working actively on couple of projects to support the security community. As you all may already know that we have successfully completed our reversing and malware analysis training programme and we are very glad that it was very helpful for everyone. In my opinion the success of any […]
Advanced Malware Analysis Training Sessi...
Here is the quick update on this month’s Local Security meet (SX/Null/G4H/owasp) and our advanced malware training session on (Part 2) Dissecting the HeartBeat RAT Functionalities This is part of our FREE ‘Advanced Malware Analysis Training’ series started from Dec 2012. In this extended session, I explained “Decrypting various Communications Of HeartBeat […]
Advanced Malware Analysis Training Sessi...
Here is the quick update on this month’s Local Security meet (SX/Null/G4H/owasp) and our advanced malware training session on (Part 1) Reversing & Decrypting Communications of HeartBeat RAT This is part of our FREE ‘Advanced Malware Analysis Training’ series started from Dec 2012. In this extended session, I explained “Decrypting The […]
Our Local Security Meet [19th October 20...
Talks: 09:30 – 10:00: WebSockets for Beginners – Prasanna K WebSockets is definitely one of the brighter features of HTML5. It allows for easy and efficient real-time communication with the server,. It’s very useful when you’re developing an interactive application like chat, game, real time reporting system etc. From a security standpoint there are many […]