Here is the delightful news for all JDownloader fans. We have just released new version of JDownloader Password Decryptor v2.0 which supports password recovery from latest JDownloader 2 Beta edition. Over the last couple of months we have received numerous requests to support JDownloader 2 beta version. Some of them even sent us account config […]
You are browsing archives for
Category: Computer Security
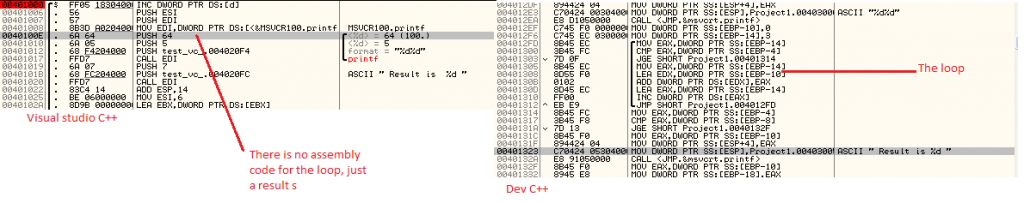
Demystifying Compiler Optimization – Dif
I analyzed some simple source code examples running in visual C++ (without optimization option) and Dev C++. I saw that VC++ code is slightly optimized then DEV C++. The following code shows the difference between function calls on both the compilers. In visual C++: push eax mov ecx, [local.1] push ecx call F Dev C++: […]
nullcon Security Conference Delhi 2012 H...
We at nullcon feel proud to be at the forefront of the IT Security arena in the Asian IT Industry. With the fourth event in the row, we continue to deliver the latest and responsible vulnerability disclosures and their mitigation solutions which help organizations take proactive and timely protective measures to safeguard their critical data […]
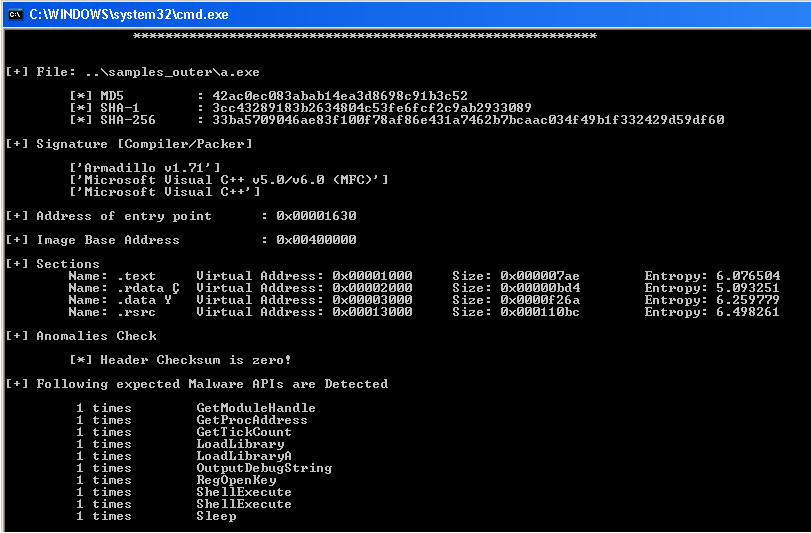
Malicious binary abusing Maths sin funct...
Couple of days ago one of my friend sent me a malicious binary. The binary was using an interesting technique for self decryption and execution. The technique itself is not new and not widely known because of its dependency on the operating system but it was interesting to see how it was executing its payload. […]
Metasploit Penetration Testing Cookbook ...
I am happy to share about the release of my first book , “Metasploit Penetration testing Cookbook”. After a dedicated effort of 10 months and strong support from the SecurityXploded community, my project finally completed on time. The book is published under Packt publishing house and is available on all major online stores like amazon, […]
Training Session Part 9 – Practical Reve
Here is the quick update from our this month’s Local Security meet (sx/null/g4h/owasp) where Monnappa delivered a splendid session on ‘Practical Reversing (IV) – Advanced Malware Analysis’. This is part of our ongoing FREE ‘Reversing & Malware Analysis Training’ started since our Jan 2012 meet. In this interesting practical session, he explained the malware […]
Using ShellDetect for Shellcode Analysis...
Some people queried me about ShellDetect specifically, how it works or how they can use it for shellcode analysis and detection. Shelldetect is the result of a short term research programme, I was actually trying to build a tool that can detect shellcode using the dynamic analysis apart from applying GetPC heuristics or some similar […]
Announcing Results for the Student Mento...
We are very glad to announce the results of our mentorship programme. In the selection process we first shortlisted the participants on the basis of the answers they provided for questionnaire. The shortlisted candidates were then interviewed by the experts. On the basis of their comments following students are selected for this programme. […]
Nullcon Delhi [2012] Security Conference
Nullcon Delhi, 4th International Security Conference” on 26 – 29 Sep 2012 at The Leela Kempinski , Gurgoan, brings together CXOs, Security Researchers, IT Professionals and Senior Management in a collaborative environment to present and discuss issues relating to IT security. The conference would be attended by eminent representatives of the Information Security domain, leaders […]
Training Session Part 8 – Practical Reve
Here is the quick update from our this month’s Local Security meet (sx/null/g4h/owasp) where Monnappa delivered a splendid session on ‘Practical Reversing (III) – Memory Forensics. This is part of our ongoing FREE ‘Reversing & Malware Analysis Training’ started since our Jan 2012 meet. In this interesting practical session, he explained the process of memory […]