SXPasswordSuite is the complete collection of all the FREE password recovery softwares released by SecurityXploded.com. It contains latest version of all the password tools which makes it easy for the user to get all these tools at one place without worrying about downloading each of them separately. . As of now it has total of […]
Blog
CryptoCode: Base64 Decoder
In previous blog posts I had written about MD5 & SHA256 Hash generation algorithms as well as DES Encryption/Decryption methods using Windows Cryptography Functions. Today I am going to present a crypto program for Base64 Decoder – very popular encoding algorithm. . Base64 is commonly used along side the encryption/decryption algorithms as a double layer […]
My ‘Community Talk’ at PES Institute
Today was another great day as I spent first half of my day delivering speech to M.Tech students at PES Bangalore, one of the leading Engineering Institute in India. I always cherished those moments connecting with students, inspiring and motivating them to do better than what I did. . This opportunity stuck when our former […]
Official Launch of Our First Linux Tool ...
Finally we have decided to officially launch our first Linux tool, FireMasterLinux. It is the Linux port of our popular tool FireMaster, a Firefox master password recovery tool. FireMaster is the first ever built tool to recover the lost master password of Firefox. . In order to protect the stored login passwords, Firefox uses master […]
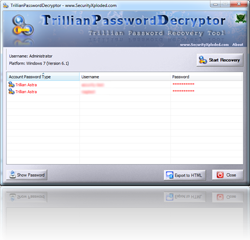
New Password Recovery Tool – TrillianPas
Recently we have released couple of dedicated password recovery tools for various instant messengers such as DigsbyPasswordDecryptor & PaltalkPasswordDecryptor. Today we are releasing yet another tool, TrillianPasswordDecryptor for popular instant messenger Trillian. . Trillian is the most popular universal messenger with rich 450+ features. It supports almost all IM clients including Gtalk, Windows Live, AIM, […]
CryptoCode: DES Encryption & Decryption
In previous posts, I wrote example code for generating MD5 Hash & SHA1 Hash using Windows Cryptography Functions. Here I am going to write about DES encryption/decryption algorithm with SHA1 based Hash key generated using Password. This is most common way of generating password where in unique data is used to generate a Hash Key […]
CryptoCode: Generate SHA1/SHA256 Hash u...
In my previous blog post on ‘Generating MD5 Hash’, I wrote code example on creating MD5 hash. Today I will be presenting the direct code sample for generating SHA1 hash using Windows Cryptography functions. Due to various collision problems with MD5 Hash, now a days SHA256 hash is used more extensively for unique identification. The […]
CryptoCode: Generate MD5 Hash using Win...
Here I have decided to put together series of Crypto sample using Windows Cryptography functions as well as OpenSSL library. This is to make it easier for myself as well as others to find ready to use cryptography code examples. Though some of these code samples are present some where on the net, I am […]
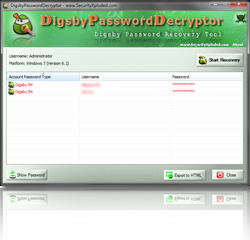
DigsbyPasswordDecryptor : New Password R...
DigsbyPasswordDecryptor is the new password recovery software to instantly recover all stored account passwords by Digsby. Digsby is one of the popular instant messenger of recent times with IM client, Email Notification & Social Networking all in one software. Digsby has a multi protocol IM client that lets you chat with all your friends on […]
Book of the Month – Mobile Malware Attac
As mobile devices becoming more and more sophisticated with their computing power and memory, the attackers are slowing shifting their focus from PC to these Mobile devices. Unlike earlier generation of mobile devices, current mobile devices are as powerful as our computer systems with increased memory and performance along with built-in internet connectivity. All of […]