I am writing this blog to share my SecurityXploded Student Mentorship Programme experience with the future students of this programme. My mentorship programme started last year in August when I was in 2nd year of MS at IIIT-Allahabad. I knew about SecurityXploded community since I used to follow their blogs, training programmes and security tools […]
You are browsing archives for
Author: Sameer Patil
Code Injection and API Hooking Technique...
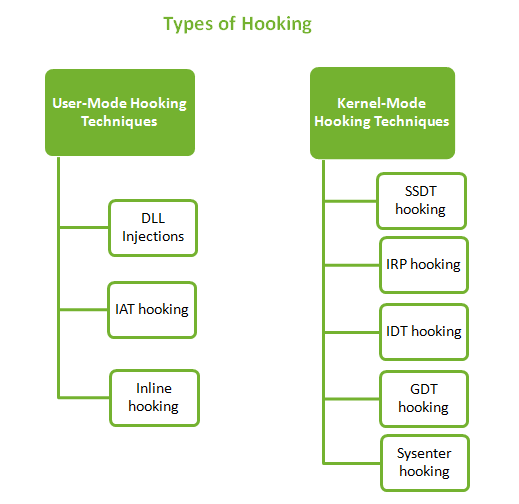
Hooking covers a range of techniques used for many purposes like debugging, monitoring, intercepting messages, extending functionality etc. Hooking is also used by a lot of rootkits to camouflage themselves on the system. Rootkits use various hooking techniques when they have to hide a process, hide a network port, redirect file writes to some different […]
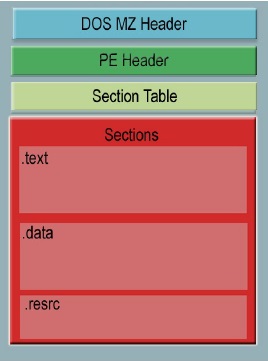
Detailed Overview and Internals of PE Fi...
A win32 portable executable(PE) file consists of: DOS Header, PE Header, Section Table, Sections. Analyzing a PE file gives us a lot of information like the address in memory where the file will be located (ImageBase), address of entry point, imported and exported functions, packed or unpacked etc. Thus this static analysis can indicate whether […]
Using PEB to Get Base Address of Kernelb...
Process Environment Block (PEB) is a user mode data structure which applies over a whole process. It is designed to be used by the application-mode code in the operating system libraries, such as NTDLL.dll, Kernel32.dll. Through the use of PEB one can obtain the list of loaded modules, process startup arguments, ImageBaseAddress, heap address, check […]
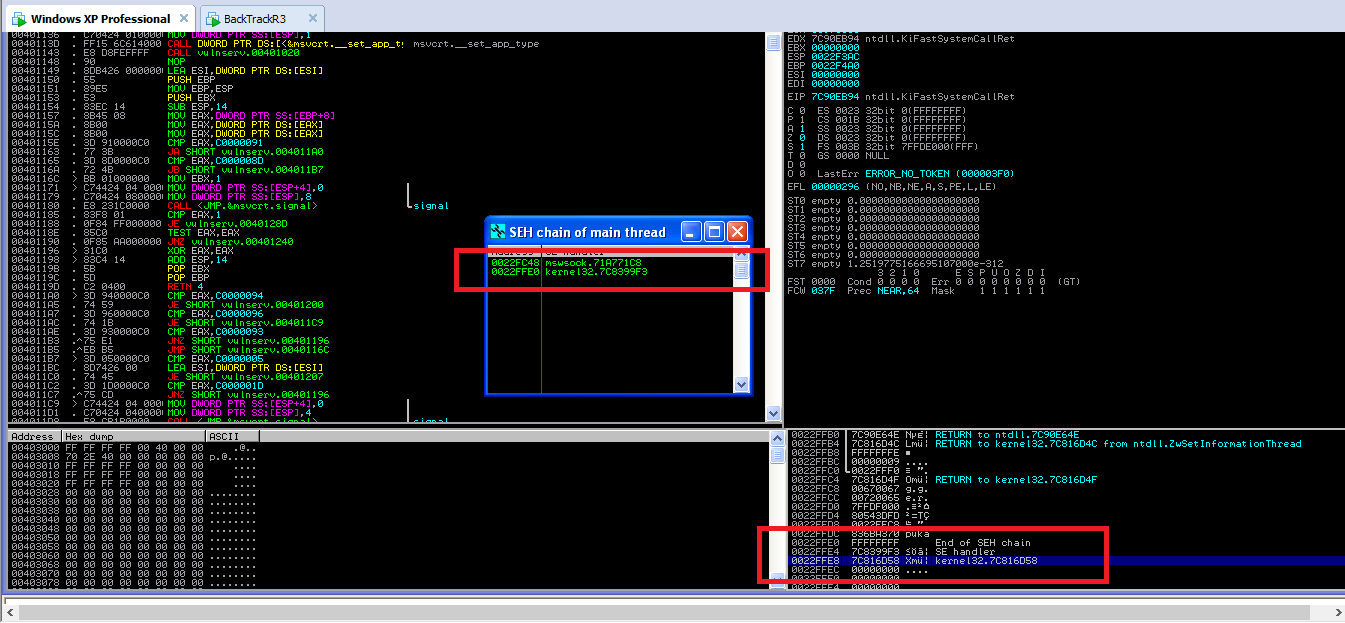
SEH Exploitation to Get Shell Access
Structured Exception Handling is a mechanism for handling both hardware and software exceptions in Windows OS. Structured exception handling enables us to have complete control over the handling of exceptions and it also provides support for debuggers as well. SEH exploitation is based on stack buffer overflow technique. It becomes easy to exploit a […]