Windows uses registry to store every user and policy configuration on the system. One can directly tweak anything in the registry to alter any of the system settings. However not all registry keys are visible when viewed through default registry editor (regedit.exe). Especially some of the security and core system related keys are hidden from user. Even administrator cannot see these special keys.
Here are some of the such hidden registry keys
HKEY_LOCAL_MACHINE\SECURITY
HKEY_LOCAL_MACHINE\SAM
SECURITY registry key stores all the system policy and LSA secrets related information. SAM registry key has details for user accounts along with LM/NTLM password hashes for each user.
There are many ways we can view these hidden registry keys. We can use psexec.exe tool (part of pstools package from sysinternals) to launch the regedit.exe as system account as shown below.
psexec.exe -s -i regedit.exe
Here is the screenshot showing the hidden SAM accounts through registry editor running under system account.
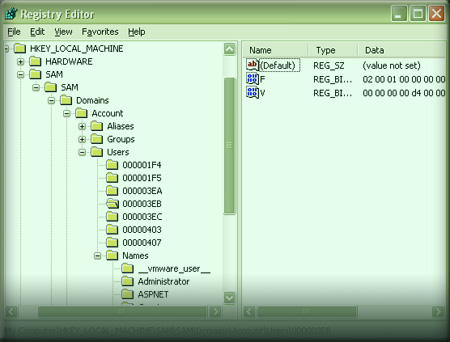
Another way to view these hidden keys is through IceSword, the antirootkit tool. This beautiful tool comes with powerful registry editor using which all these hidden registry keys can be discovered easily.
Here is the screenshot below which shows Security registry key through IceSword.
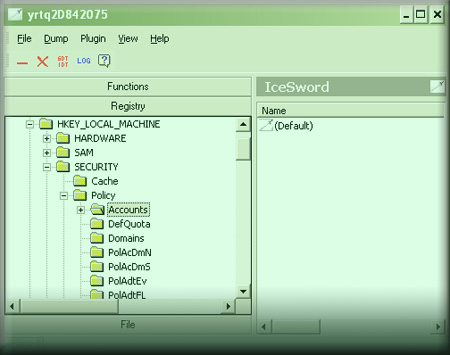
.

No Comments Yet