‘Dll Hijack’ vulnerability is one of the recently highlighted critical security issue affecting most of the popular Windows applications. Every day researchers are discovering more and more applications which are vulnerable to various forms of ‘Dll Hijacking’ and at the same time attackers have started exploiting these vulnerable applications. . In that event, we had […]
You are browsing archives for
Category: Vulnerability Research
Released DllHijackAuditor v2 with New &
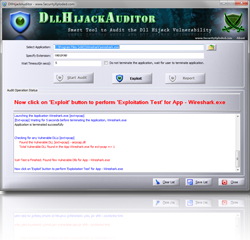
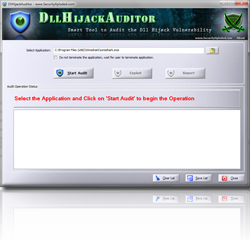
DllHijackAuditor is the FREE tool to Audit against the DLL Hijacking Vulnerability for any Windows application. This is recently discovered critical security vulnerability affecting most of Windows systems. Currently large number of applications are currently susceptible to this vulnerability which can allow any attacker to completely take over the system. . In the first version […]
Presenting DllHijackAuditor – Smart Tool
DllHijackAuditor is the FREE tool to Audit against the DLL Hijacking Vulnerability for any Windows application. This is recently discovered critical security issue affecting almost all Windows systems on the planet. It appears that large amount of Windows applications are currently susceptible to this vulnerability which can allow any attacker to completely take over the […]
Book of the Month – Cyber Fraud: Tactics
Gone are the days when those BlackHat Hackers would tickle you for fun, Now they will poke you & take your diamonds without you even knowing anything about it until it’s too late. Landscape in the Cyber underground has completely changed since then, making it more like well organized business controlled by global entities around […]
DLL Hijacking Exploit – All at One Plac
The web is full of recent DLL Hijacking Exploit after HDMoore and other security researchers have reported about numerous Windows applications suffering from these flaws. Here I have decided to put together simple version with all the relevant links at one place so that one gets the complete picture. . What is DLL Hijacking Vulnerability […]
Unleashing VASTO – A Virtualization Asse
VASTO is the first of its kind toolkit designed to asses the security of various Virtualization solutions including VMWare and Xen server. It is implemented as set of modules which can be integrated into Metasploit , the popular penetration testing framework. This makes it very easy for pen testers to directly integrate VASTO with their […]
Google Offer Rewards for Chrome Hackers
Here comes the Google’s turn to offer bounty for hackers finding bugs in Chrome. As per the latest post “Encouraging More Chromium Security Research” on its official blog of Chrome, Google has decided to follow the practice of Microsoft and other organizations to reward the security researchers. For every Security vulnerability found in Chrome, Google […]
Operation Aurora – Google Got Hacked thr
Operation Aurora – The well targeted attack under which top companies including Google got hacked through the zero day vulnerability. Google has released separate statement recently illustrating nature of the attack vectors and motives of the attacker. In this attack which believed to be originated from China, the zero day (not publicly known) vulnerability in […]
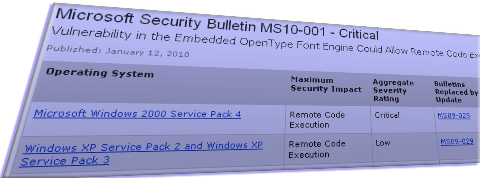
M$ Patches First Security Vulnerability ...
M$ has announced its first critical security vulnerability of the year 2010 in its Tuesday patch release. This is the vulnerability in the OpenType font engine embedded in the client applications which can lead to remote code execution leading to complete control of the system. As per the bulletin, the attack can be simulated by […]
End of Exploit Empire – milw0rm.com
As in the matrix, Everything which has beginning has an end, something similar happened to the matrix theme based milw0rm.com, the top exploit publishing website. Created in 2003 by a hacker who is known as ‘str0ke’, milw0rm.com has served the exploits for around 6 years and it has been popular source of exploits for the […]