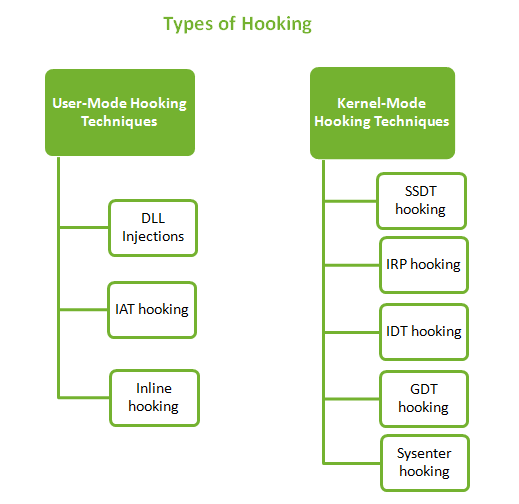
Hooking covers a range of techniques used for many purposes like debugging, monitoring, intercepting messages, extending functionality etc. Hooking is also used by a lot of rootkits to camouflage themselves on the system. Rootkits use various hooking techniques when they have to hide a process, hide a network port, redirect file writes to some different […]
You are browsing archives for
Category: Rootkits
Reversing Training Session Part 12 – Roo
Here is the quick update on this month’s Local Security meet (SX/Null/G4H/owasp) where Monnappa has delivered one of the best session of our entire series on ‘Rootkit Analysis’. This is part of our ongoing FREE ‘Reversing & Malware Analysis Training’ started since our Jan 2012. Monnappa delivered splendid session today. In this session, he talked […]
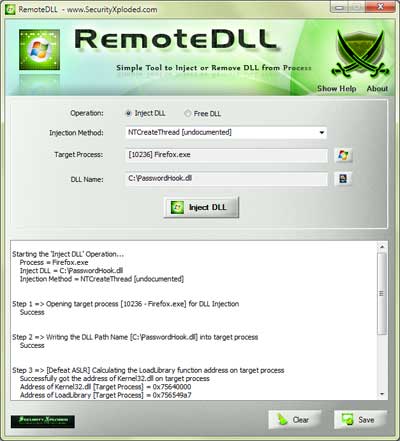
Released RemoteDLL v2 – Simple Tool to I
Finally I am happy to write this post on the mega version of RemoteDLL. It took me around 5 years to bring this new version of RemoteDLL with all those envisioned features. I was more excited when it worked just right on Windows 8 inspite of changes around DLL structure, thanks to cut back mechanism […]
Book of the Month – Malware Analyst’s Co
“Malware Analyst’s Cookbook” is the latest master piece in the Malware Analysis field which covers almost all facets of the subject from all possible angles. I haven’t seen any book like this which covers everything that Malware Analyist will ever need starting from basics to advanced analysis. . . Here is the core information about […]
Video on SpyDllRemover Detecting HxDef R...
Few days ago, we have released the major version 4.0 of SpyDllRemover which featured significant enhancements over the previous versions. In order to show case all the features properly we have decided to create a series of video demonstrations which will help user to understand & use the SpyDllRemover to its full potential. . . […]
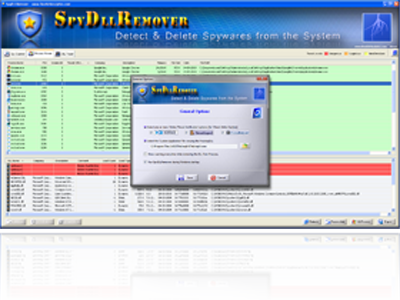
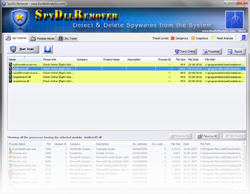
Released SpyDllRemover Mega Version v4.0
SpyDllRemover is the specialized tool for detecting spyware & hidden Rootkit Dlls in the System. It can also detect & remove user-land Rootkit processes as well as other spyware processes using multiple [user-land] Rootkit detection algorithms coupled with in-house Process heuristics. This makes it a generic tool for detecting & removing any known as well […]
Be a Player in Beta Testing of SpyDllRem...
As we approach the finishing line of next major release of SpyDLLRemover v4, we are planning to open it for private beta testing. The main goal is to figure out as many issues as possible and receive early feed backs from the community. We want to prevent any silly issues showing up after we hit […]
Update on Upcoming Release of SpyDLLRemo...
We have been busy working on lot of things amid of next major release of SpyDLLRemover as mentioned in previous posts. We also planned for minor update on StreamArmor. Here is the brief update on each of these tools. SpyDllRemover 4.0 We were right on schedule for last week mega release of SpyDllRemover but due […]
Book of the Month – Cyber Fraud: Tactics
Gone are the days when those BlackHat Hackers would tickle you for fun, Now they will poke you & take your diamonds without you even knowing anything about it until it’s too late. Landscape in the Cyber underground has completely changed since then, making it more like well organized business controlled by global entities around […]
Update on Next Version of SpyDLLRemover
Here is the brief update on upcoming release of SpyDLLRemover. Most of the major work highlighted in our previous blog post has been completed and only some final art work is left out. Below is the fresh glimpse of new banner which is going to replace old one. Just being the old, other reason for […]