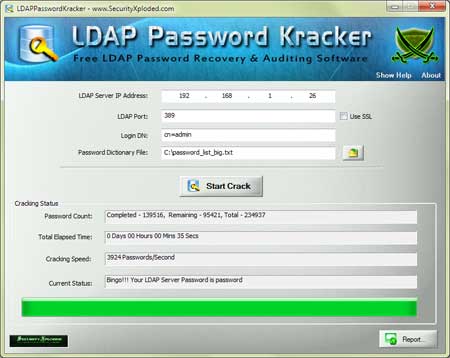
Here comes our 91st new tool – LDAP Directory Kracker . Useful tool to recover the lost password from any of the LDAP based Directory Servers.
Many companies, universities use Directory Servers to store sensitive information such as employee account details, salary, trade secrets etc. In this direction, this tool can greatly help Penetration testers to find wealth of secret details by exposing weak user passwords.
It can recover the lost password from all of these popular LDAP Directory Servers
- Novell eDirectory
- Microsoft Active Directory
- Open LDAP Directory
- Sun One Directory
- Netscape Directory
- IBM Lotus Domino
- Oracle Directory
- OpenDS Directory
It comes with elegant and user friendly interface like most of our tools. It supports Dictionary Crack method and comes with default password list file.
For more interesting details kindly visit LDAP Directory Kracker

No Comments Yet