Couple of days ago one of my friend sent me a malicious binary. The binary was using an interesting technique for self decryption and execution. The technique itself is not new and not widely known because of its dependency on the operating system but it was interesting to see how it was executing its payload.
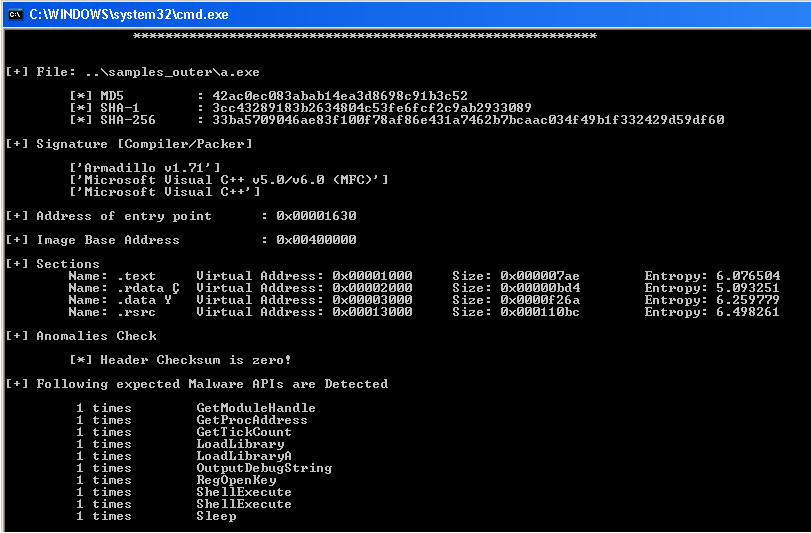
When I passed the exe to ExeScan, I got the following information.
As you can see in the image, ExeScan reports that the binary is armadillo packed but I am not sure because I have not seen such type of stuff in armadillo packer or maybe I am missing some versions of armadillo. Any way lets proceed to analysis.
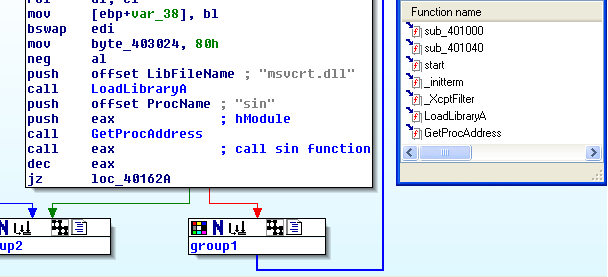
When I opened the binary in IDA, I saw that there are only two functions and just four or five API calls. You can see the same in the picture below.
Both functions are relatively small and one of the functions is using a loop in which it is calling maths sin function. So it is a clear indication that at some point binary will execute its payload through sin function. The loop is very big and manually it will take hours to reach the execution point. I kept the tracing for 1 hour and didn’t get anything. So it is sure that there is some magic value for the sin function that will lead us to payload execution. I hooked the sin function to get the magic parameter, let the binary run and note down the last argument to sin function and exactly that argument will be our magic value because after that execution goes somewhere else instead of returning to the big loop.
Hooking Code:
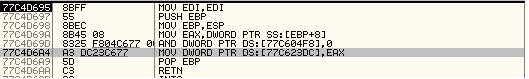
Now we know the magic value (7FF0059A) but we don’t know how it is executing its payload. If we pass the magic value to the sin function and follow the execution inside the sin function then at some point we will see the following code.
77C550D5 56 PUSH ESI 77C550D6 E8 D585FFFF CALL msvcrt.77C4D6B0 77C550DB 85C0 TEST EAX,EAX 77C550DD 59 POP ECX 77C550DE 75 08 JNZ SHORT msvcrt.77C550E8 --- --- --- 77C4D6B0 8BFF MOV EDI,EDI ; sample.004021D0 77C4D6B2 55 PUSH EBP 77C4D6B3 8BEC MOV EBP,ESP 77C4D6B5 A1 DC23C677 MOV EAX,DWORD PTR DS:[77C623DC] 77C4D6BA 85C0 TEST EAX,EAX 77C4D6BC 74 03 JE SHORT msvcrt.77C4D6C1 77C4D6BE 5D POP EBP 77C4D6BF - FFE0 JMP EAX 77C4D6C1 33C0 XOR EAX,EAX 77C4D6C3 5D POP EBP 77C4D6C4 C3 RETN
From the above code we see the following important information:
77C550D6 E8 D585FFFF CALL msvcrt.77C4D6B0
Inside function (77C4D6B0) we see an interesting instruction
77C4D6B5 A1 DC23C677 MOV EAX,DWORD PTR DS:[77C623DC]
77C623DC is a static pointer and the instruction is moving value at the pointer into EAX register and after few instructions we see the following instruction.
77C4D6BF - FFE0 JMP EAX
So it means before coming to this function our binary is also setting the static pointer (77C623DC) with its desired address then above instruction transfer the execution to that address.
If we look into the main function of the binary, we see the following instructions:
0040169E . 68 80174000 PUSH sample.00401780
004016A3 . FF15 EC204000 CALL DWORD PTR DS:[<&msvcrt.__setusermatherr>
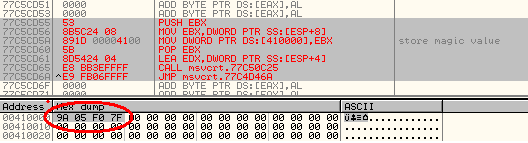
So actually “setusermatherr” function is capable of setting the static pointer (77C623DC) with the desired value. we can see the same in picture below.
In the case of our binary it will set the value at static pointer with 00401780 address.(argument to setusermatherr).
After that normal malware stuff starts which I am not interested in :).

No Comments Yet