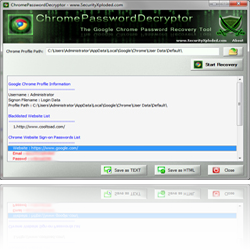
ChromePasswordDecyrptor is the Free tool to recover login passwords from Google Chrome browser. It automatically detects the login database file used by Chrome based on the version and recovers all the stored passwords.
Chrome earlier used to store the passwords in a Sqlite database file called ‘Web Data’ . But with recent version it has moved all login based database into new file called ‘Login Data’. For more details on how Chrome stores the passwords and how to recover such passwords, refer to following research article ‘Exposing the Secrets of Google Chrome’
.
New version 2.0 comes with support for recovering passwords from latest Chrome version. It also presents cool interface, better icons and good report of recovered passwords.
For more details, move on to main page of ChromePasswordDecryptor.
Thanks to everyone who has reported the issues with latest Chrome version.
.
.

No Comments Yet